Amazon Elasticache
Hands-On
Demo

In this demo, we will:
- Create an Aurora Serverless v2 MySQL cluster with sample product data
- Deploy ElastiCache Serverless for Valkey with IAM authentication
- Configure VPC networking and security groups for secure communication
- Create VPC endpoints for Lambda to access AWS services
- Build and deploy a Lambda function implementing cache-aside pattern using the official Glide client
- Test the complete system and observe performance improvements
- Monitor cache metrics and validate the caching behavior
- Clean up all resources
Agenda
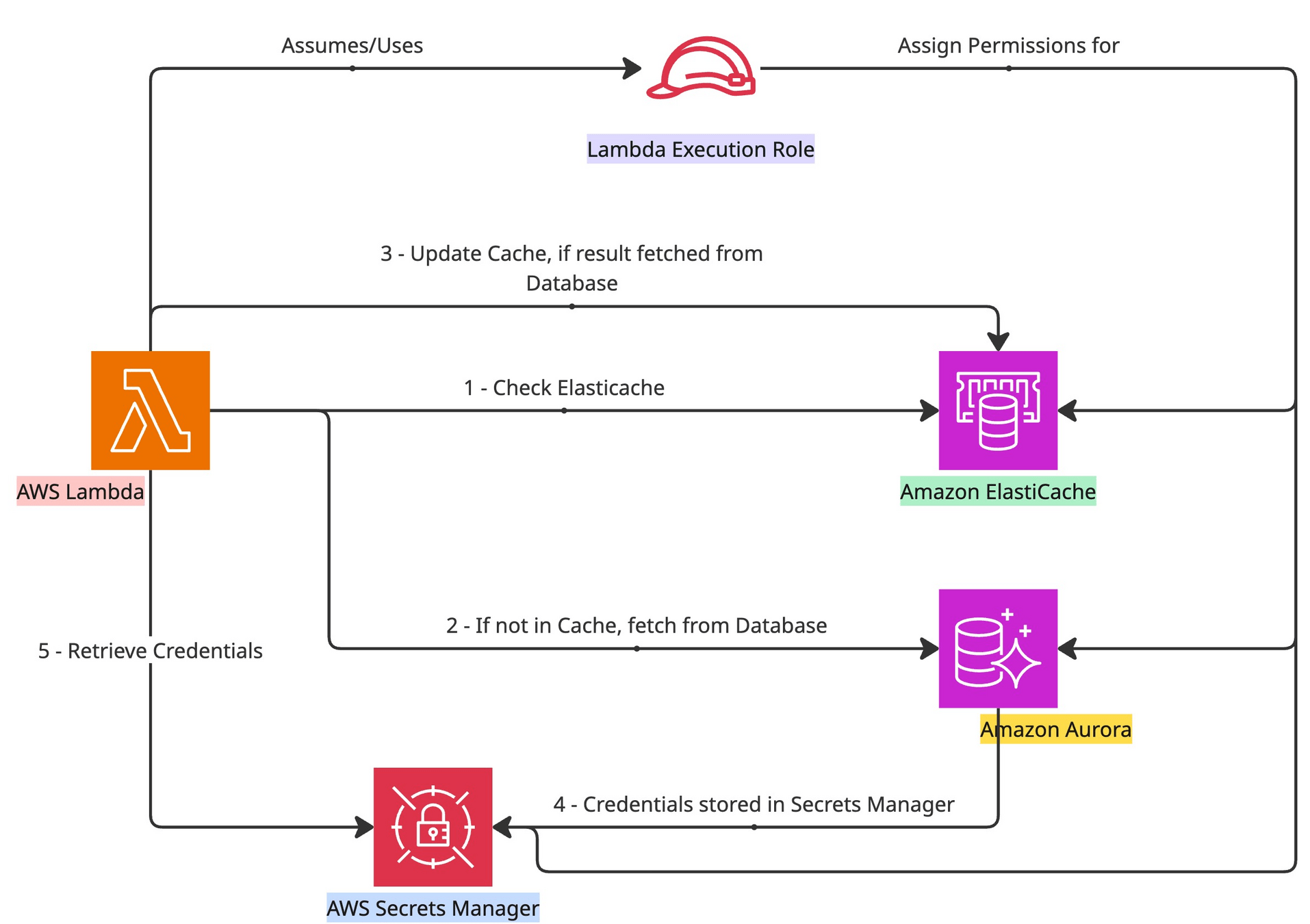
Visual Representation
Step 1: Create Aurora Serverless v2 Database
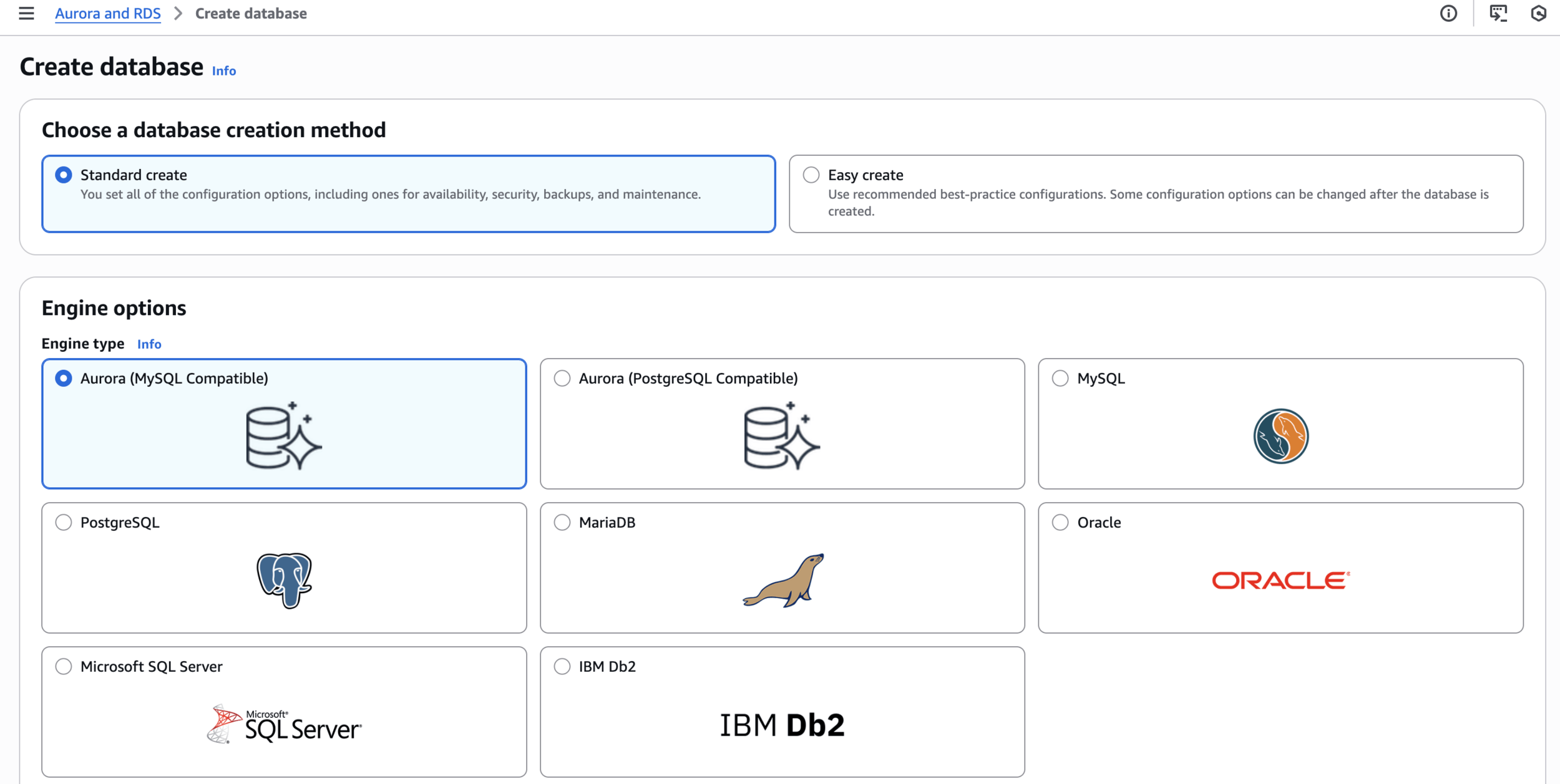
Create Aurora database
Engine version
aurora-demoadmin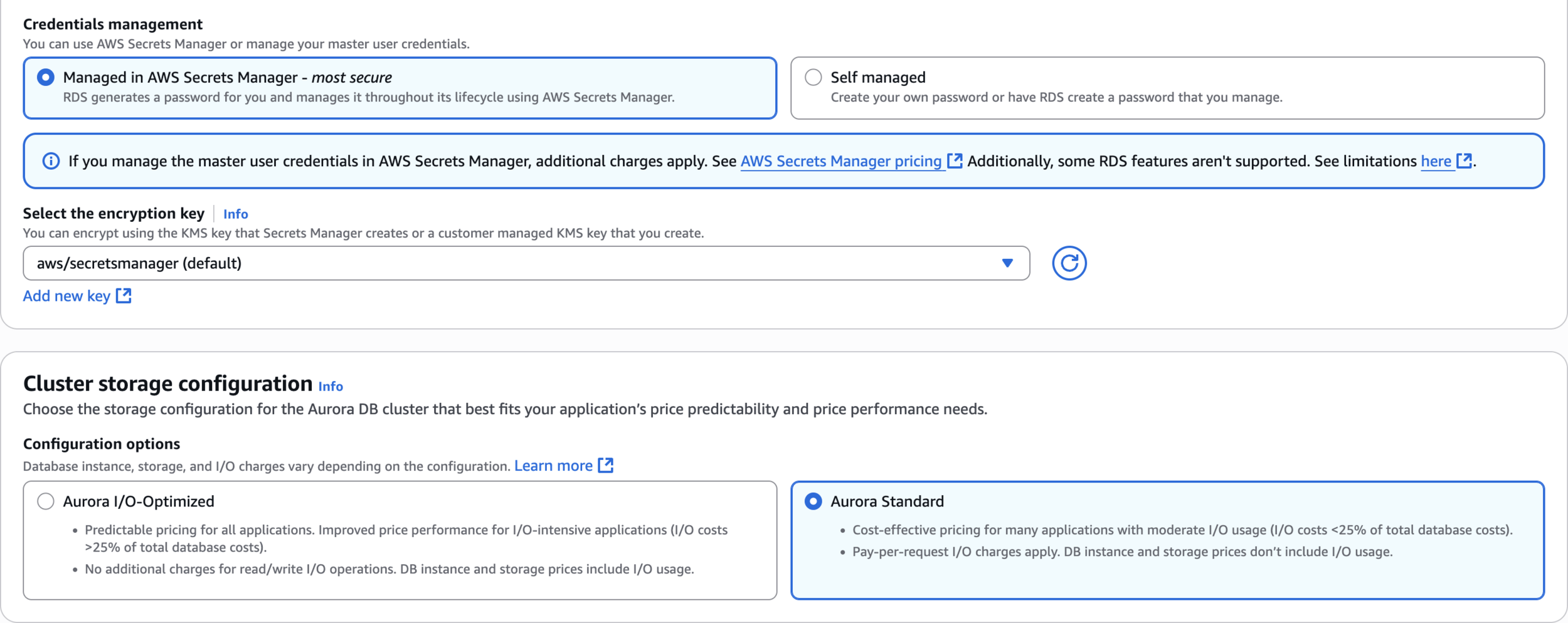
Credentials management
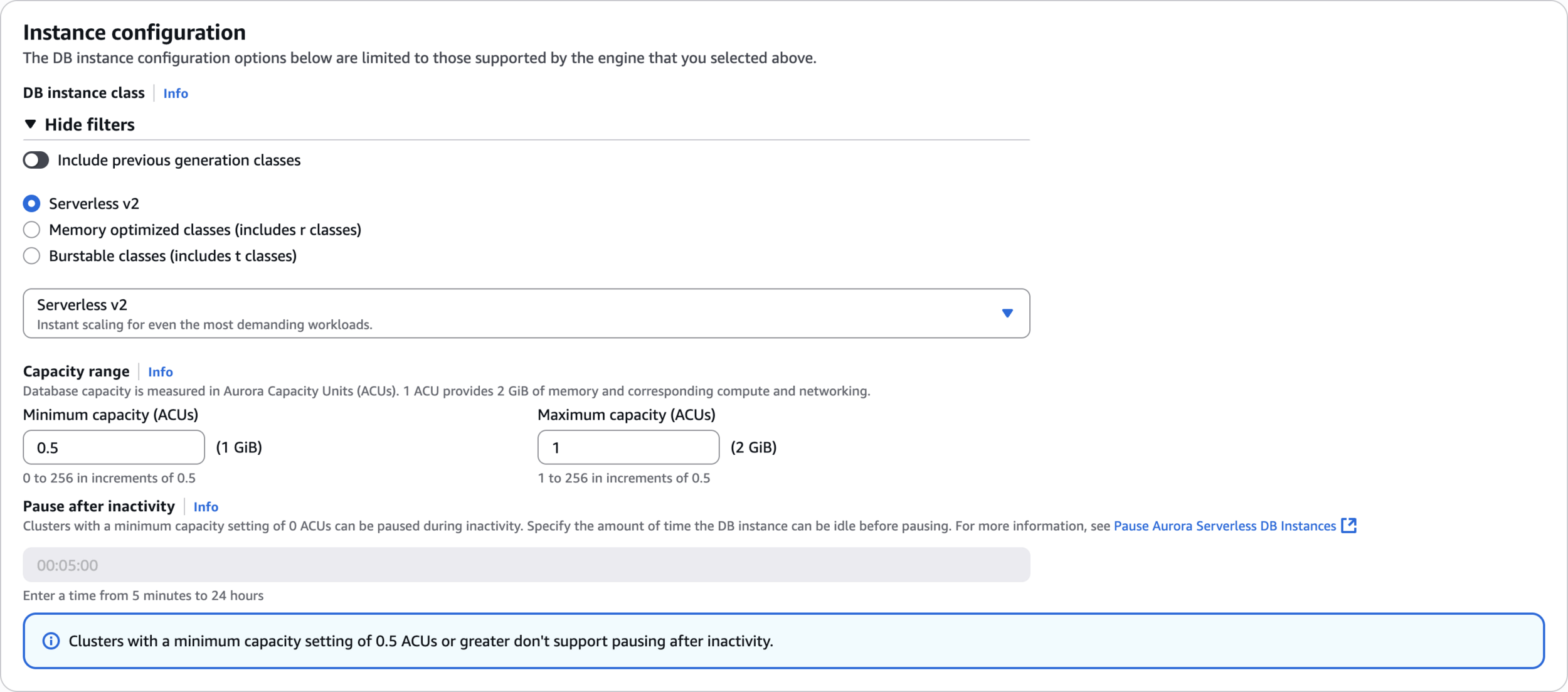
Instance configuration
0.51
Availability & durability
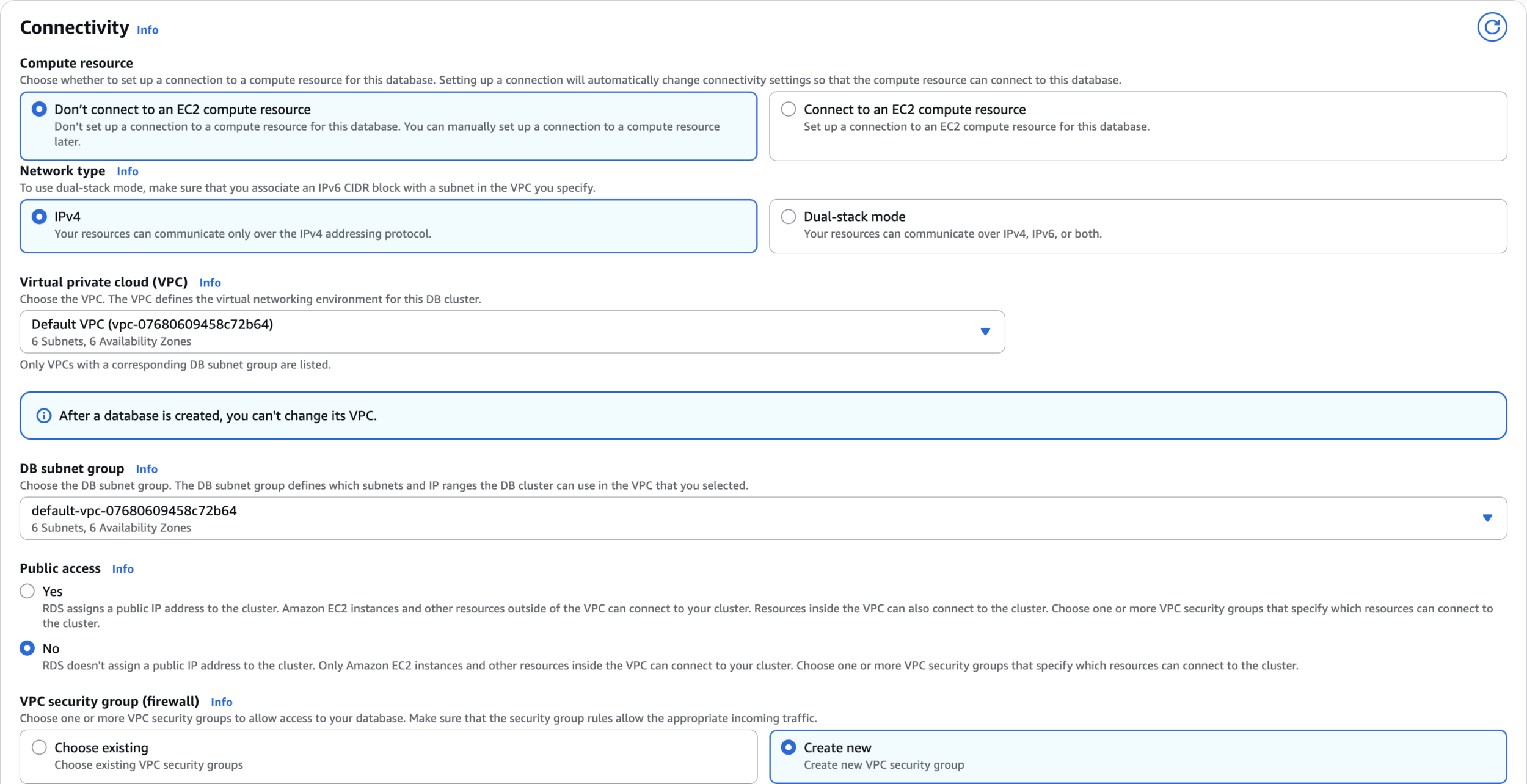
Connectivity
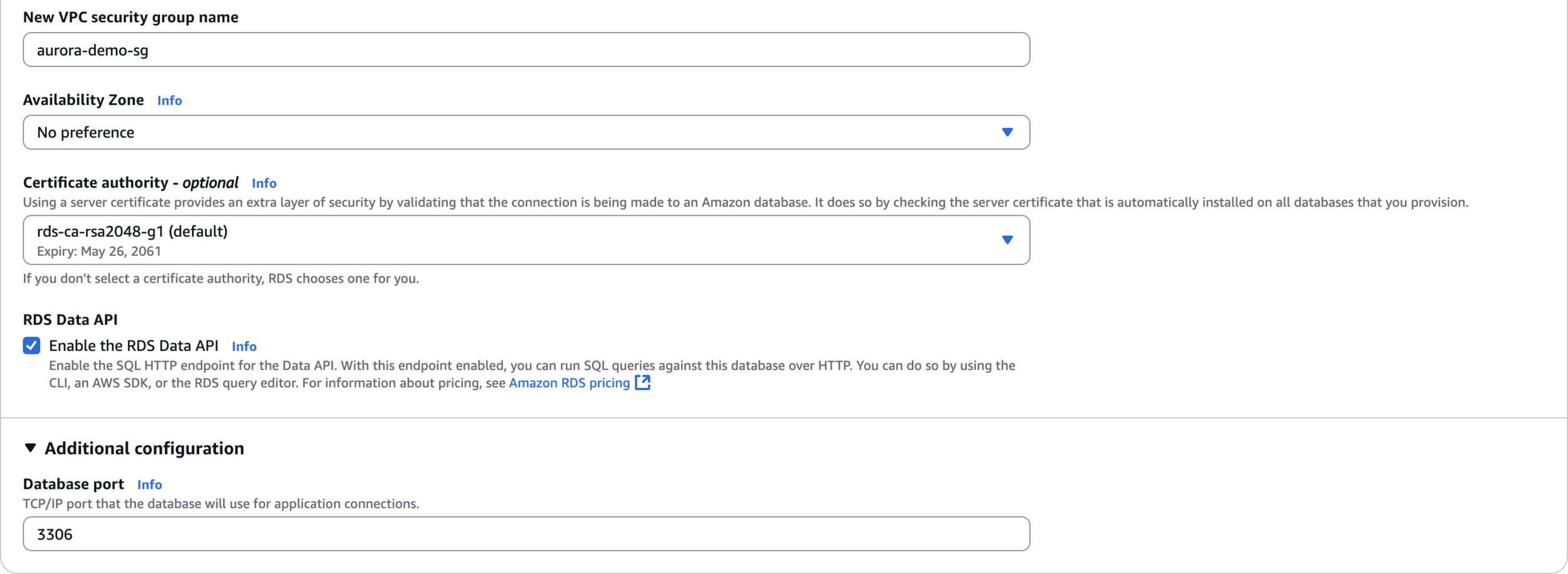
VPC security group name
aurora-demo-sg3306
Read replica write forwarding
Monitoring
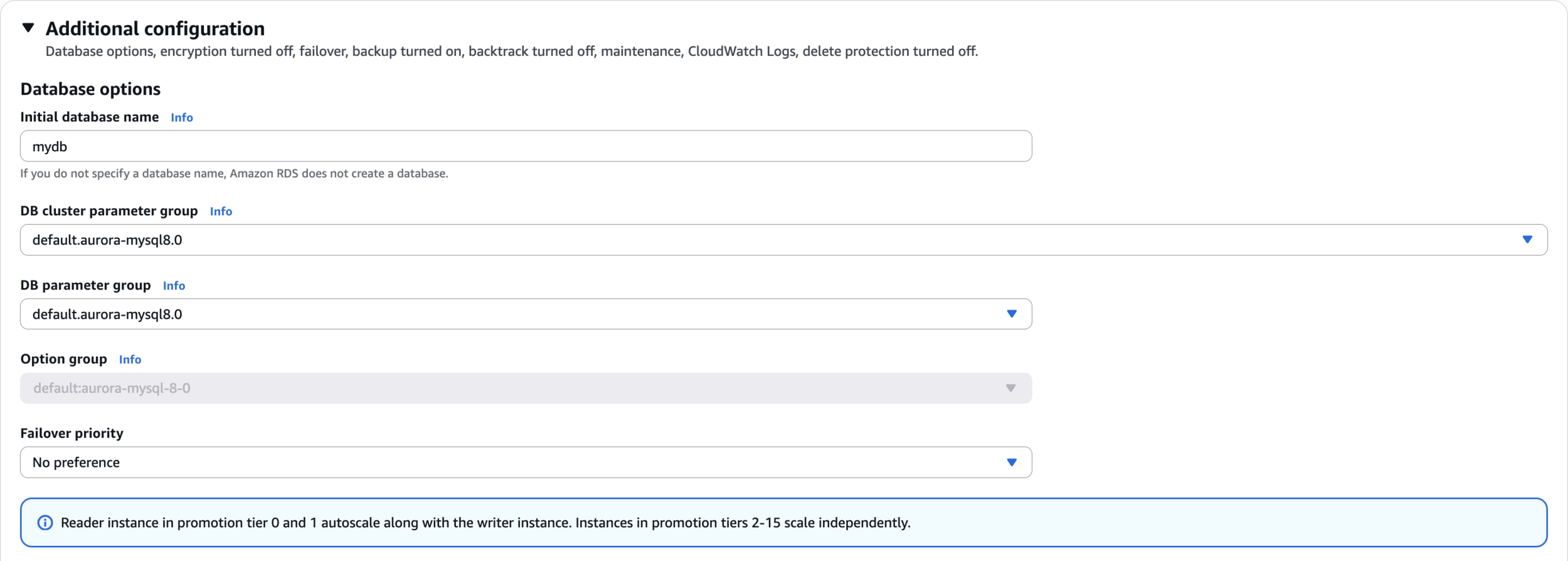
Additional configuration
mydb
Backup
Create database
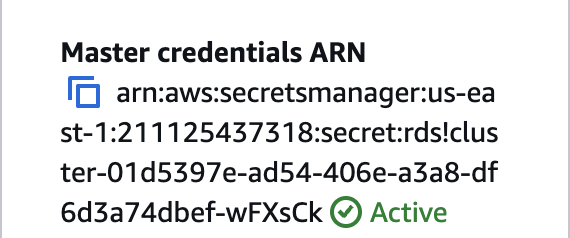
Secrets ARN
Step 2: Load Sample Data into Aurora
Load Sample Data into Aurora
AWS_PAGER=""
DB_ARN="SECRET_ARN='# Create Database if not exists
aws rds-data execute-statement \
--resource-arn "$DB_ARN" \
--secret-arn "$SECRET_ARN" \
--sql "CREATE DATABASE IF NOT EXISTS mydb;" \
--database "mysql"# Create the products table
aws rds-data execute-statement \
--resource-arn "$DB_ARN" \
--secret-arn "$SECRET_ARN" \
--sql "CREATE TABLE products(id INT PRIMARY KEY, name VARCHAR(50), price DECIMAL(6,2));" \
--database "mydb"# Insert sample data
for i in {1..20}; do
aws rds-data execute-statement \
--resource-arn "$DB_ARN" \
--secret-arn "$SECRET_ARN" \
--sql "INSERT INTO products VALUES($i, CONCAT('Widget-', $i), ROUND(RAND()*100,2));" \
--database "mydb"
done# Verify data creation
aws rds-data execute-statement \
--resource-arn "$DB_ARN" \
--secret-arn "$SECRET_ARN" \
--sql "SELECT COUNT(*) as product_count FROM products;" \
--database "mydb"Load Sample Data into Aurora
Step 3: Create ElastiCache Serverless for Valkey
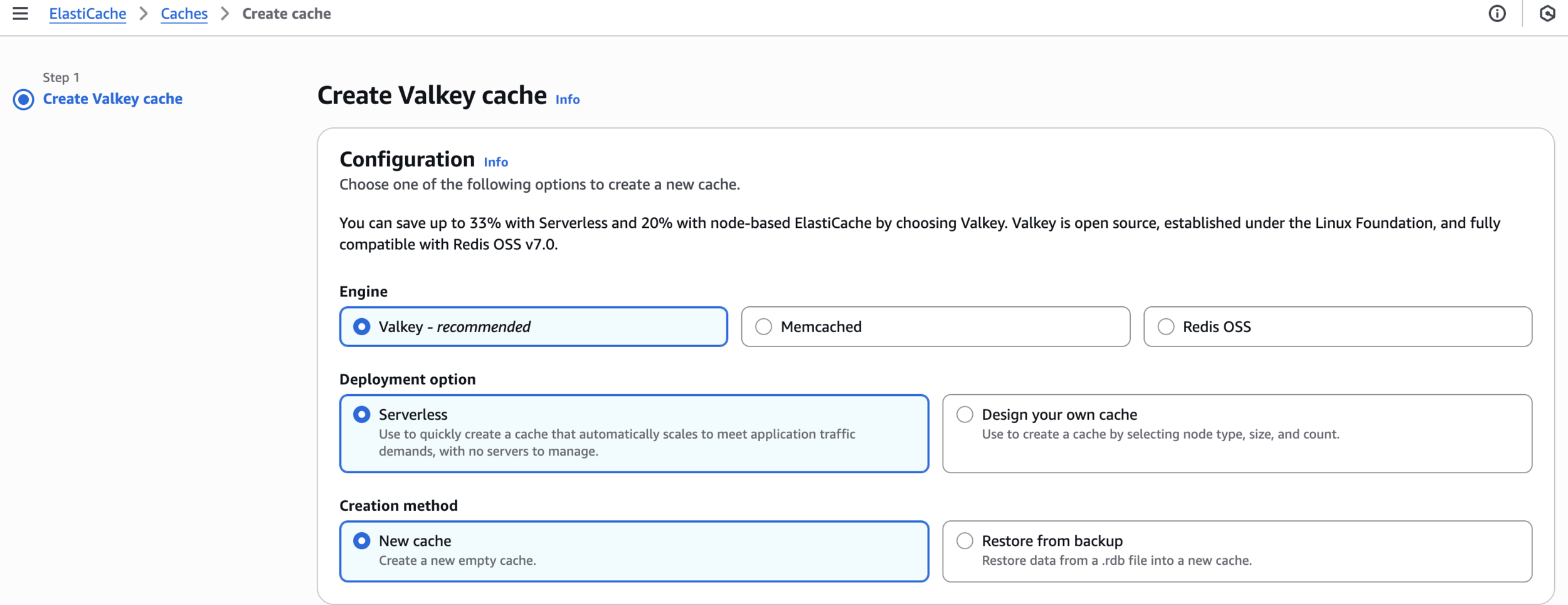
Create Valkey cache
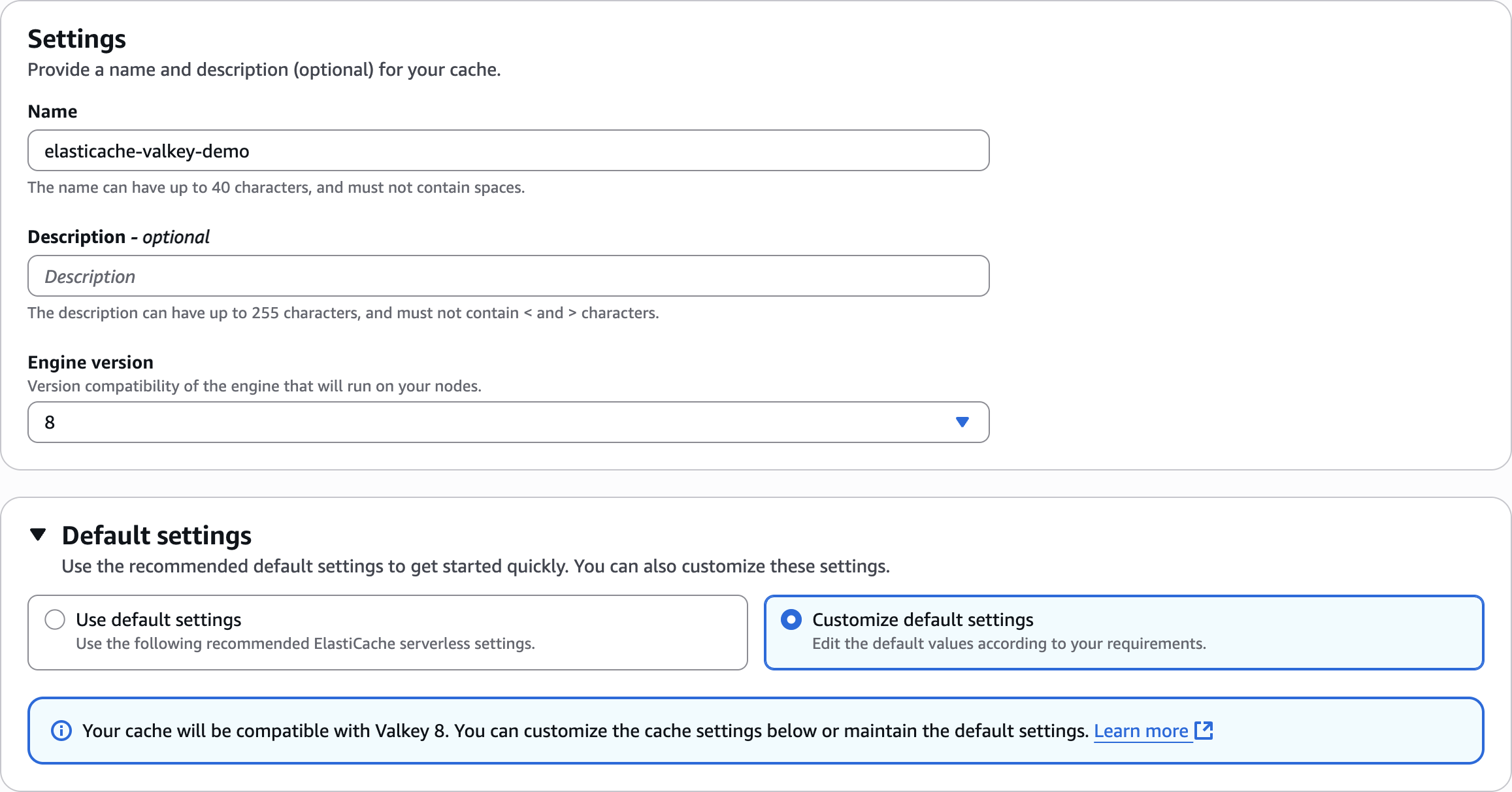
Settings
elasticache-valkey-demo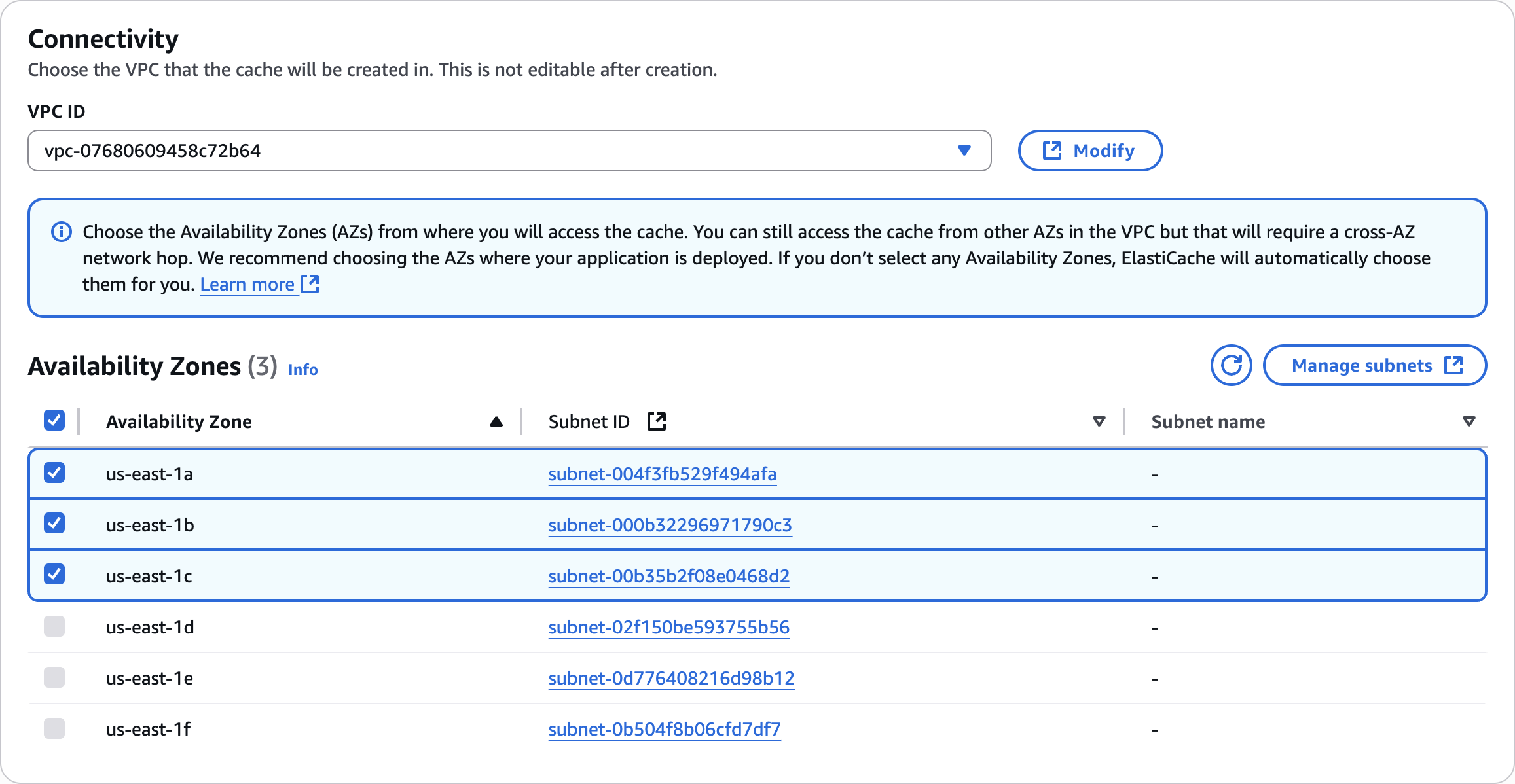
Connectivity
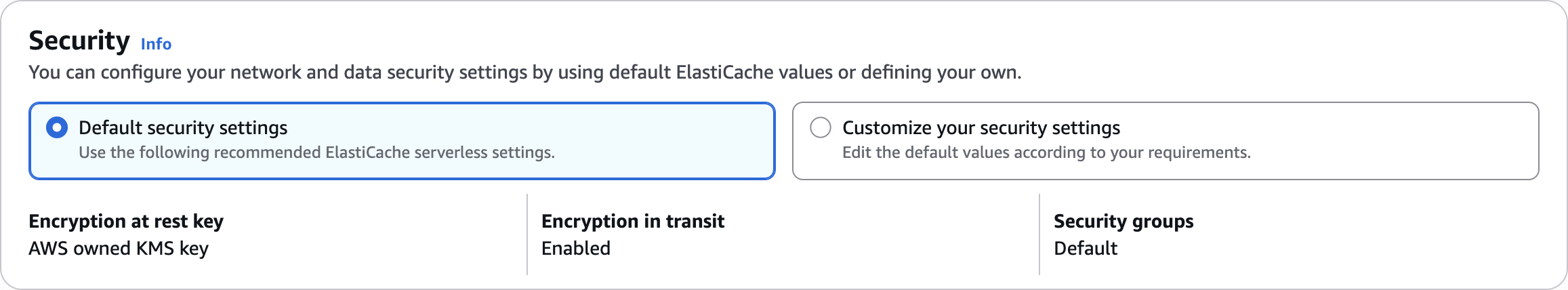
Security
Backup
Tags
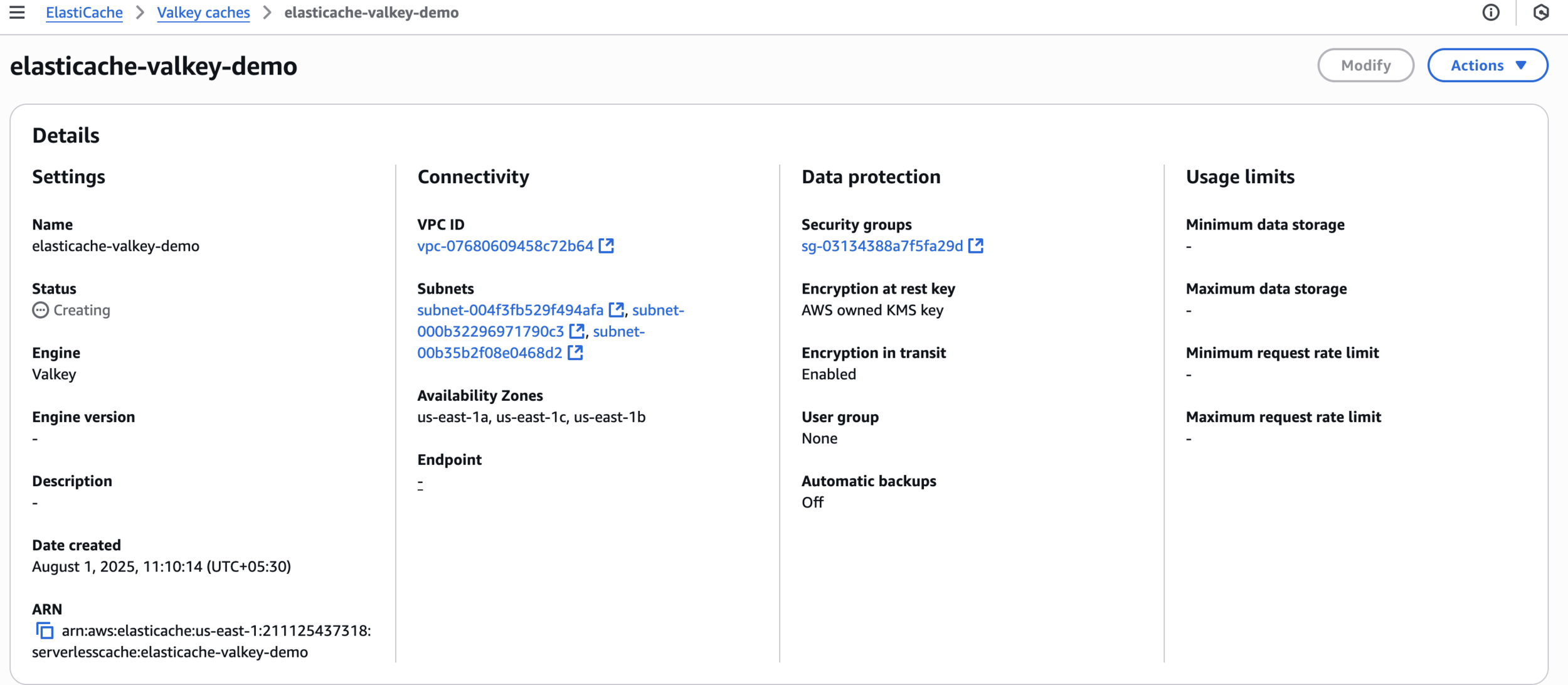
elasticache-valkey-demo
Step 4: Configure VPC Security Groups
Open ports in 2 Security Groups
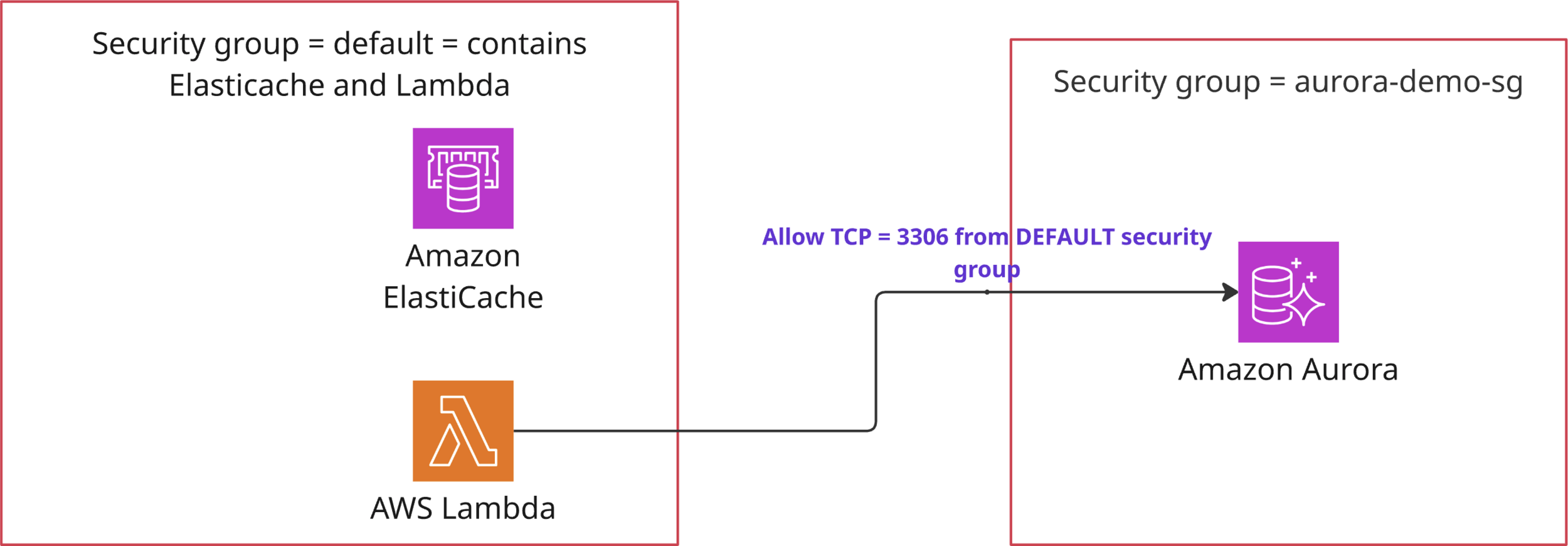
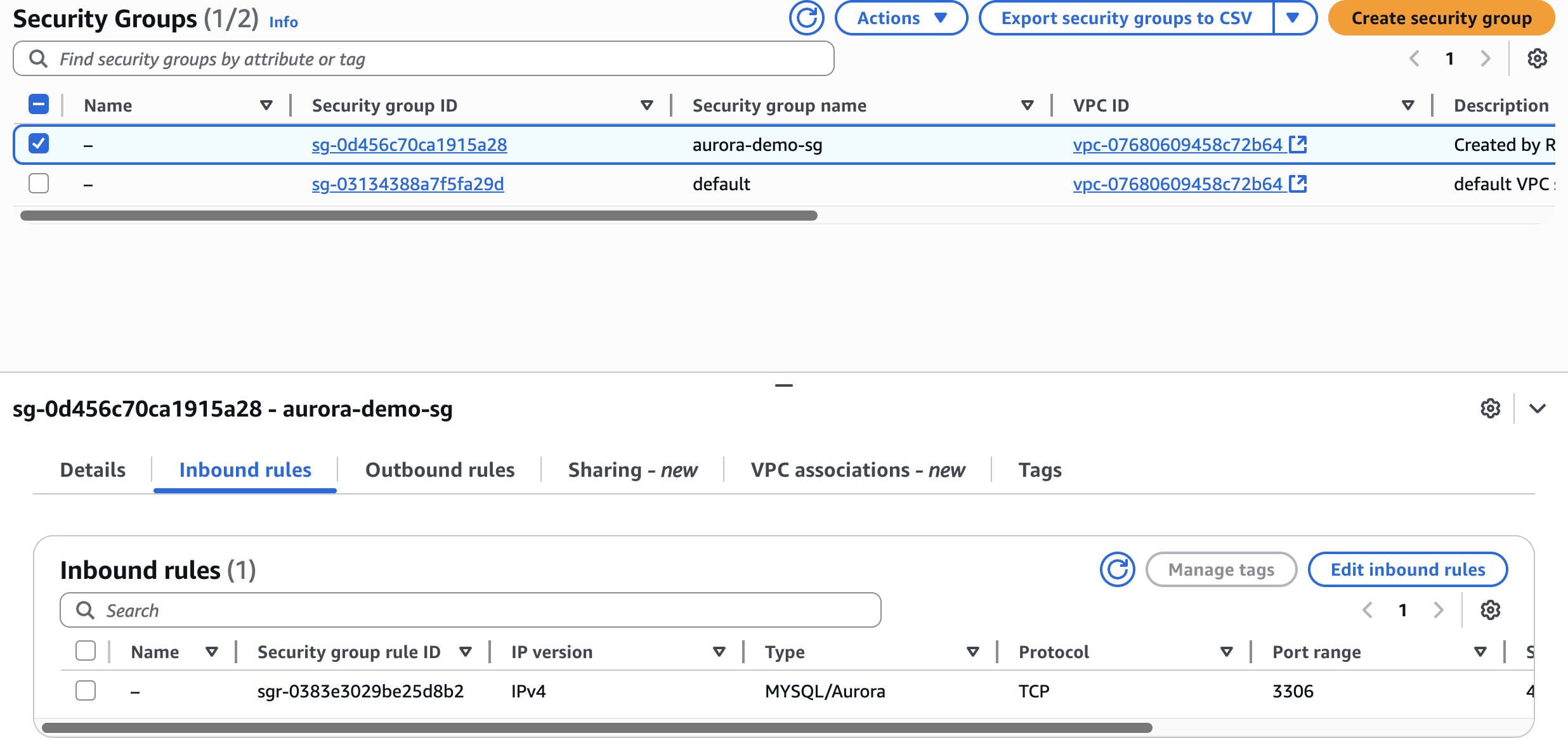
Modify Aurora Security Group
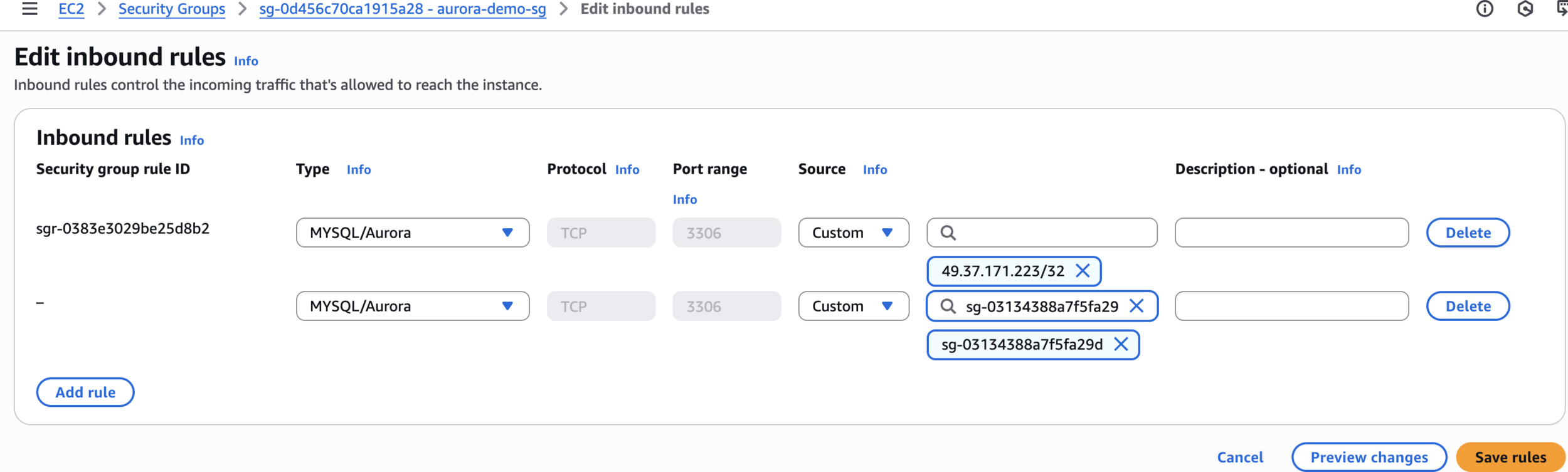
Add Traffic from Elasticache Group
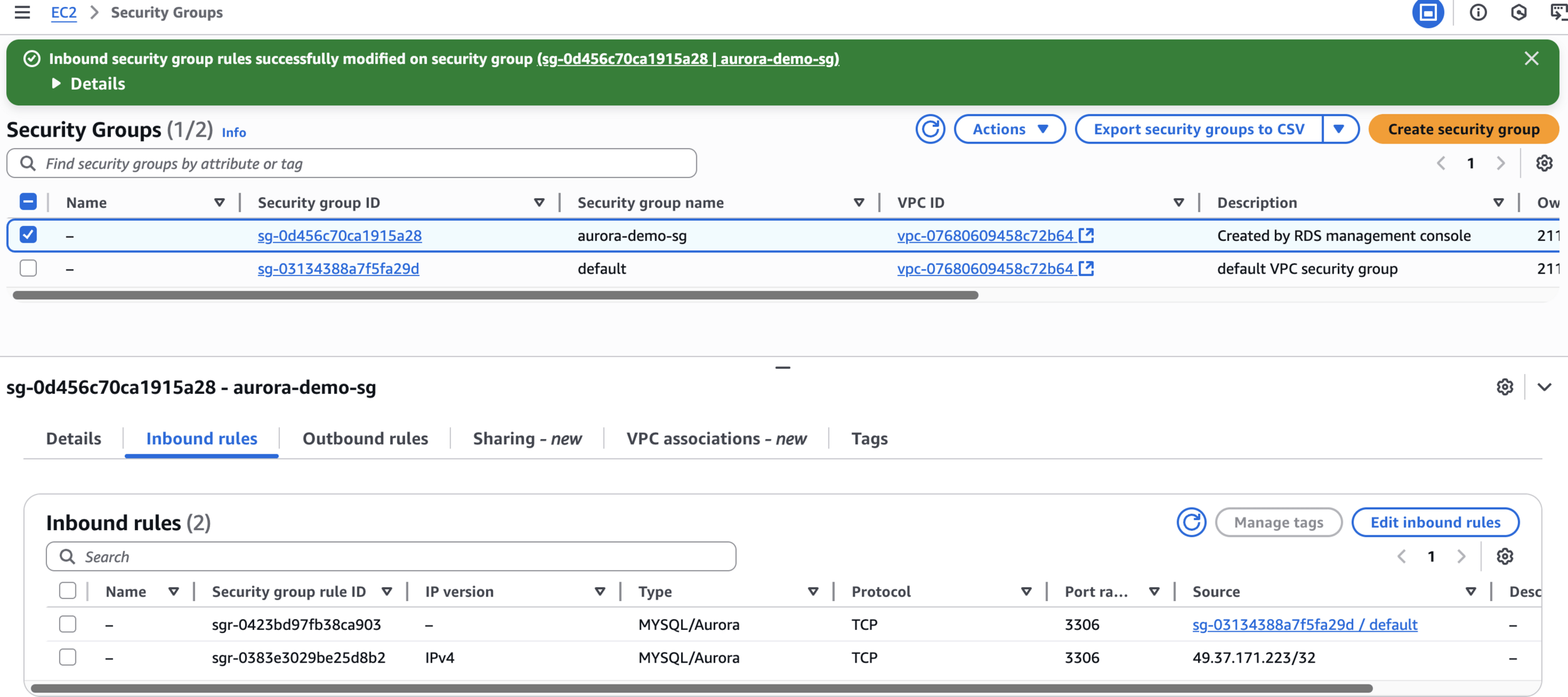
Final Settings
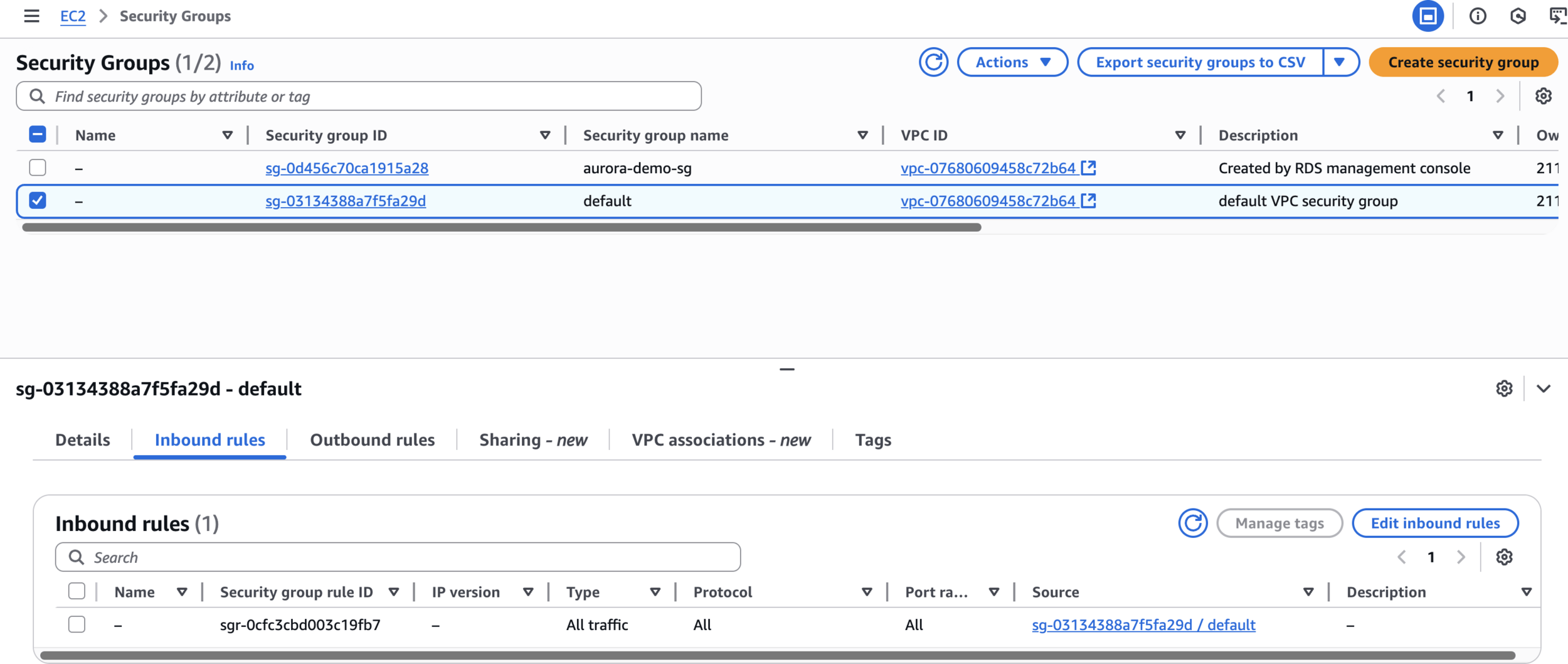
Modify Elasticache Security Group = default
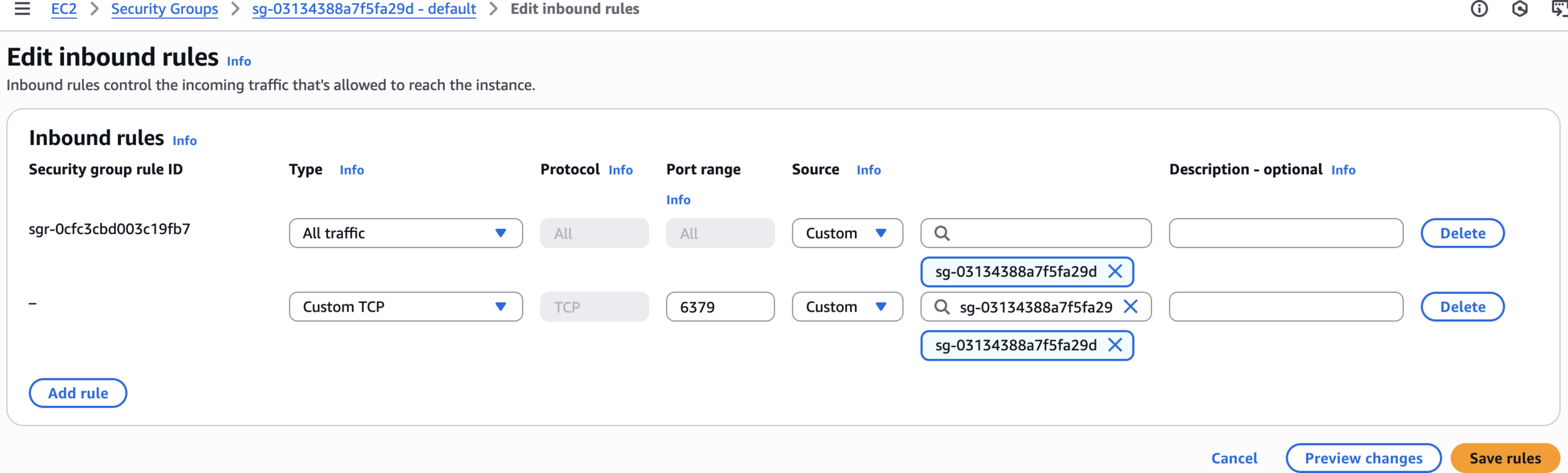
Add 6379 port or It Should be All Traffic



Final Settings
Step 5: Create VPC Endpoints for Lambda
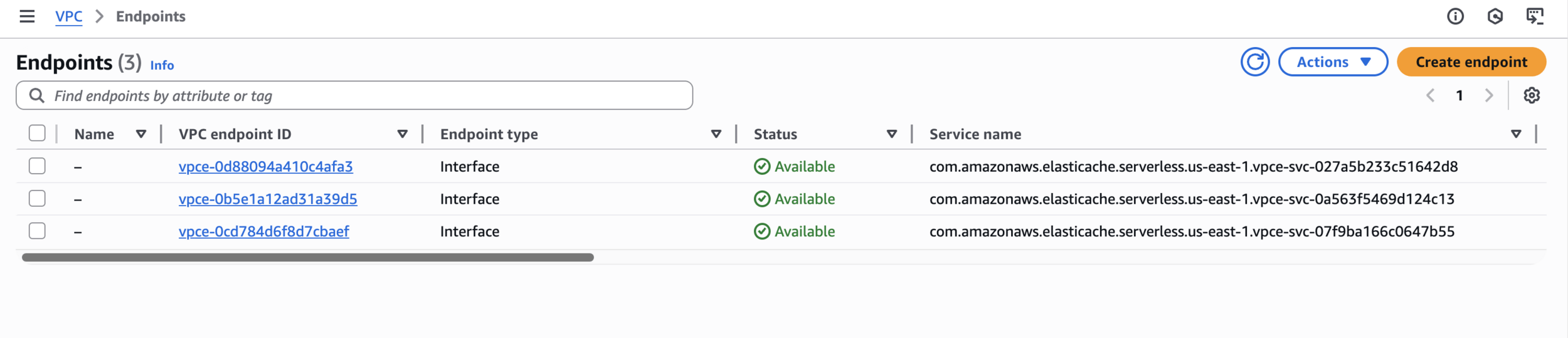
VPC Endpoints
# Get your VPC ID
VPC_ID=$(aws ec2 describe-vpcs --filters \
"Name=is-default,Values=true" \
--query 'Vpcs[0].VpcId' --output text)
# Get subnet IDs
SUBNET_IDS=$(aws ec2 describe-subnets \
--filters "Name=vpc-id,Values=$VPC_ID" \
--query 'Subnets[*].SubnetId' --output text | tr '\t' ' ')Create VPC Endpoints
# Create VPC endpoint for RDS Data API
aws ec2 create-vpc-endpoint \
--vpc-id $VPC_ID \
--service-name com.amazonaws.us-east-1.rds-data \
--subnet-ids $SUBNET_IDS \
--security-group-ids $(aws ec2 describe-security-groups \
--filters "Name=group-name,Values=default" \
--query 'SecurityGroups[0].GroupId' --output text) \
--vpc-endpoint-type Interface# Create VPC endpoint for Secrets Manager
aws ec2 create-vpc-endpoint \
--vpc-id $VPC_ID \
--service-name com.amazonaws.us-east-1.secretsmanager \
--subnet-ids $SUBNET_IDS \
--security-group-ids $(aws ec2 describe-security-groups \
--filters "Name=group-name,Values=default" \
--query 'SecurityGroups[0].GroupId' --output text) \
--vpc-endpoint-type Interface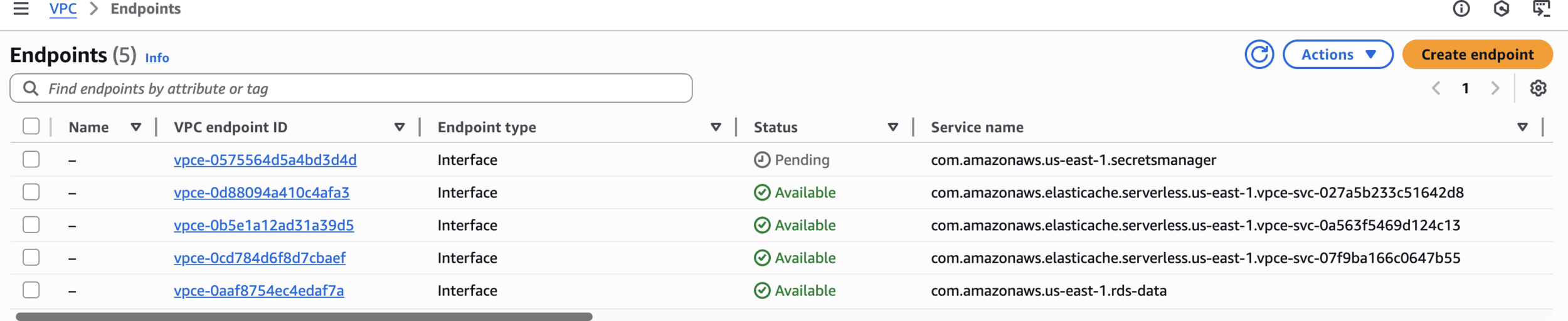
VPC Endpoints
Step 6: Create Lambda Execution Role
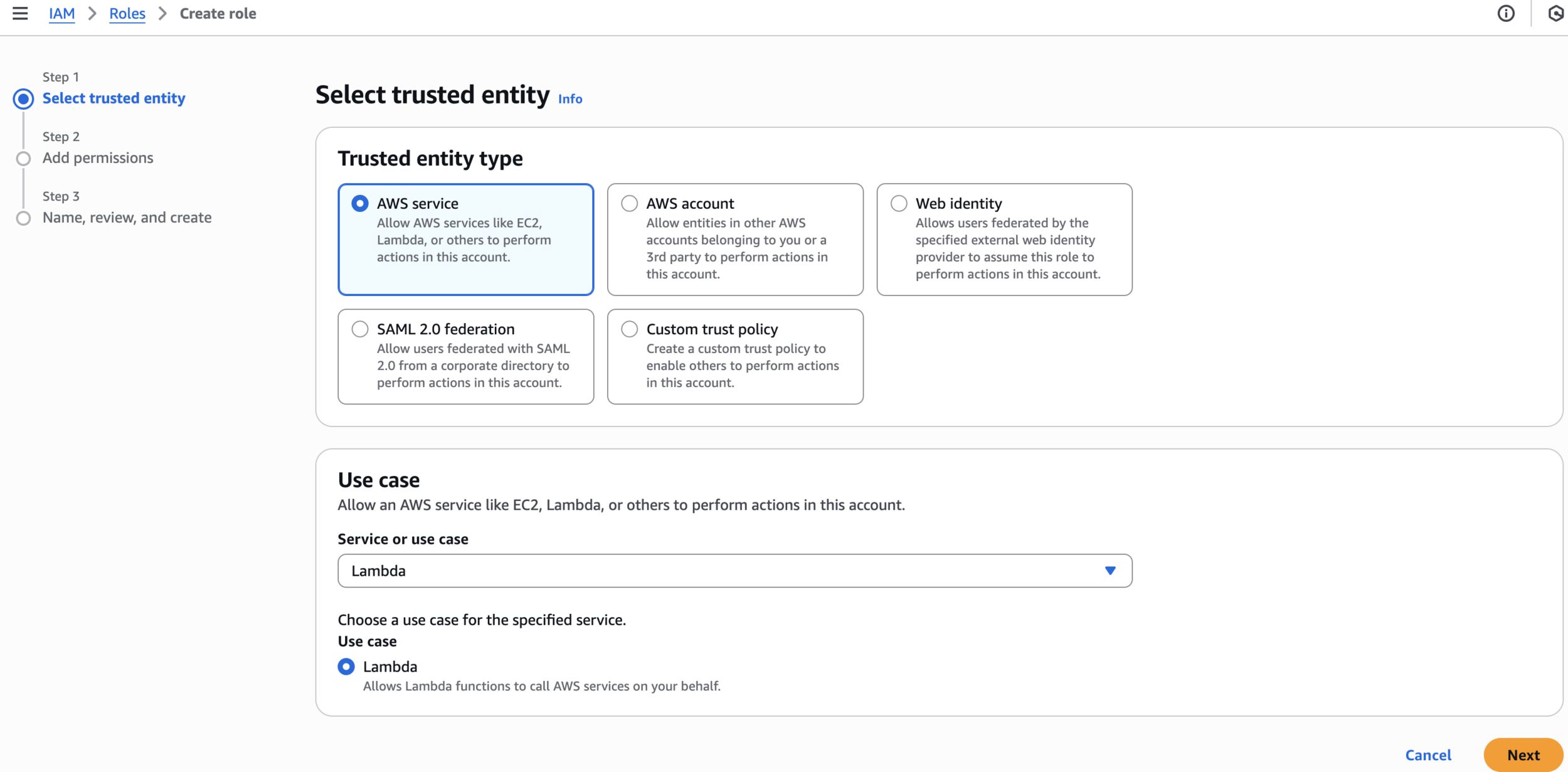
Create IAM Role
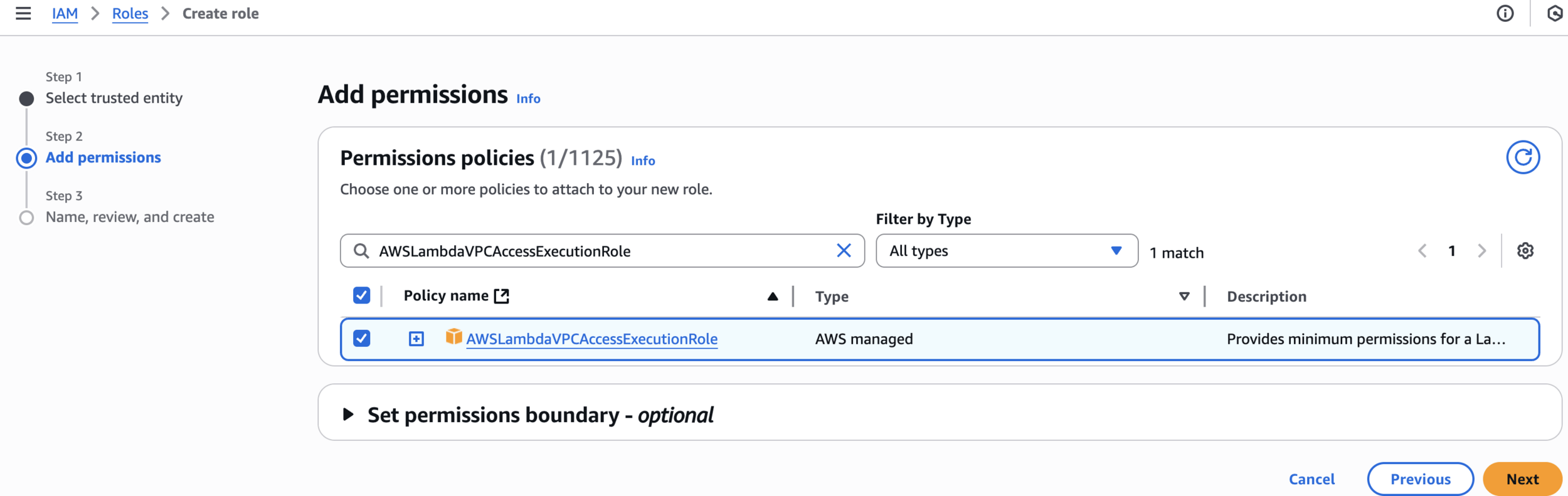
Add permissions
AWSLambdaVPCAccessExecutionRole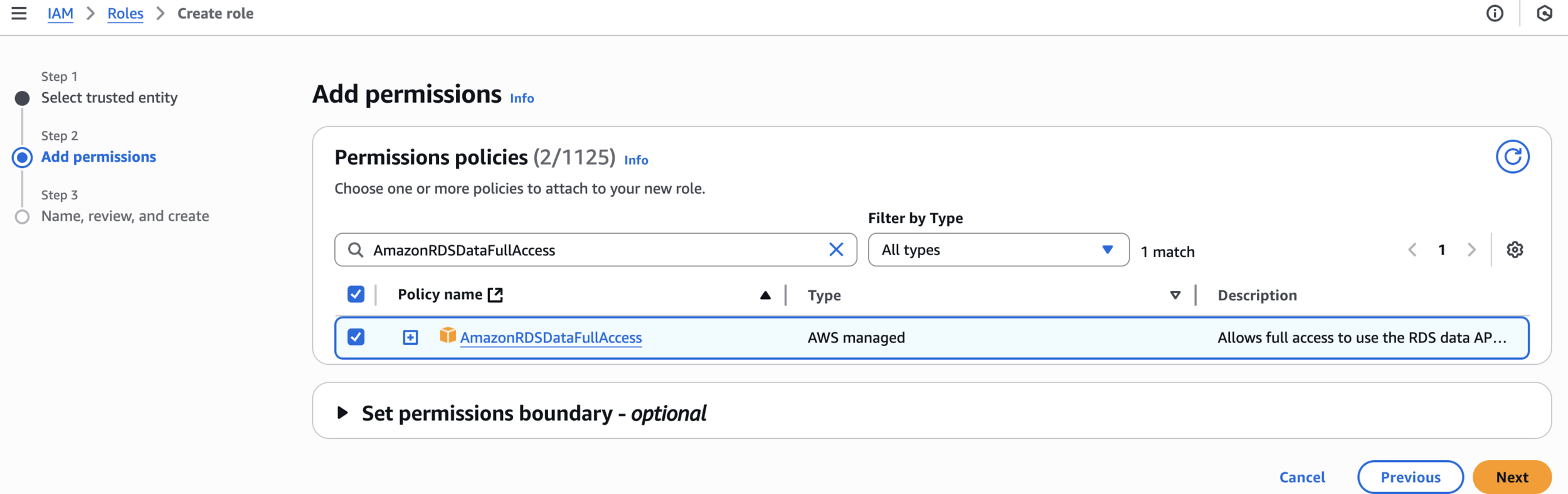
AmazonRDSDataFullAccessAdd permissions
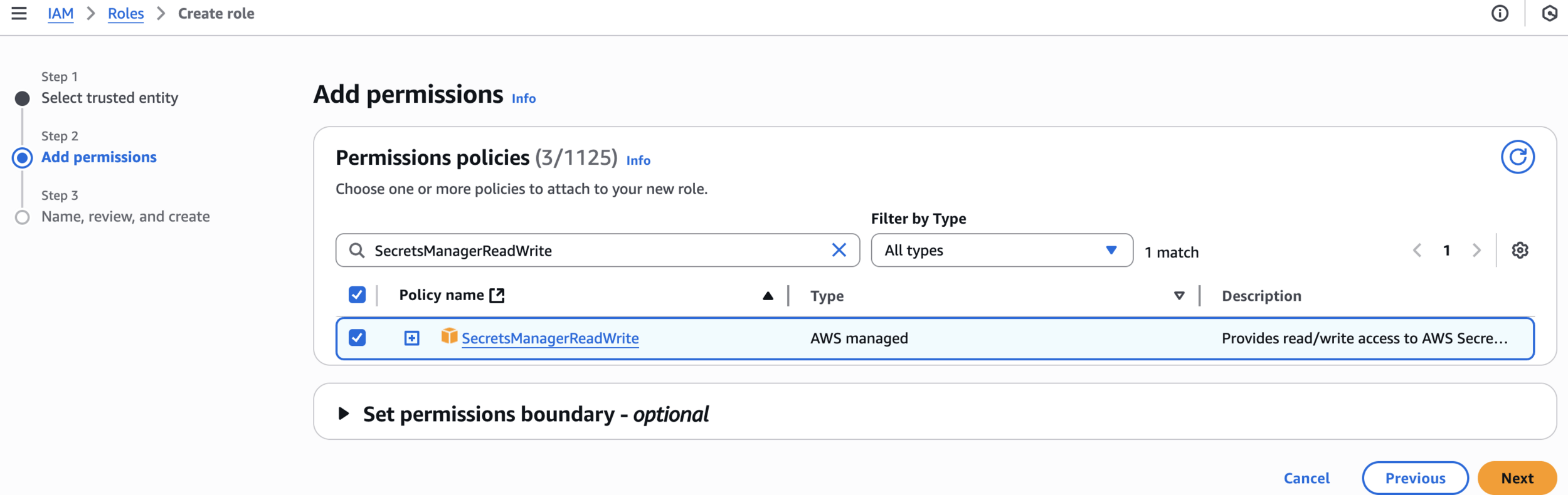
SecretsManagerReadWriteAdd permissions
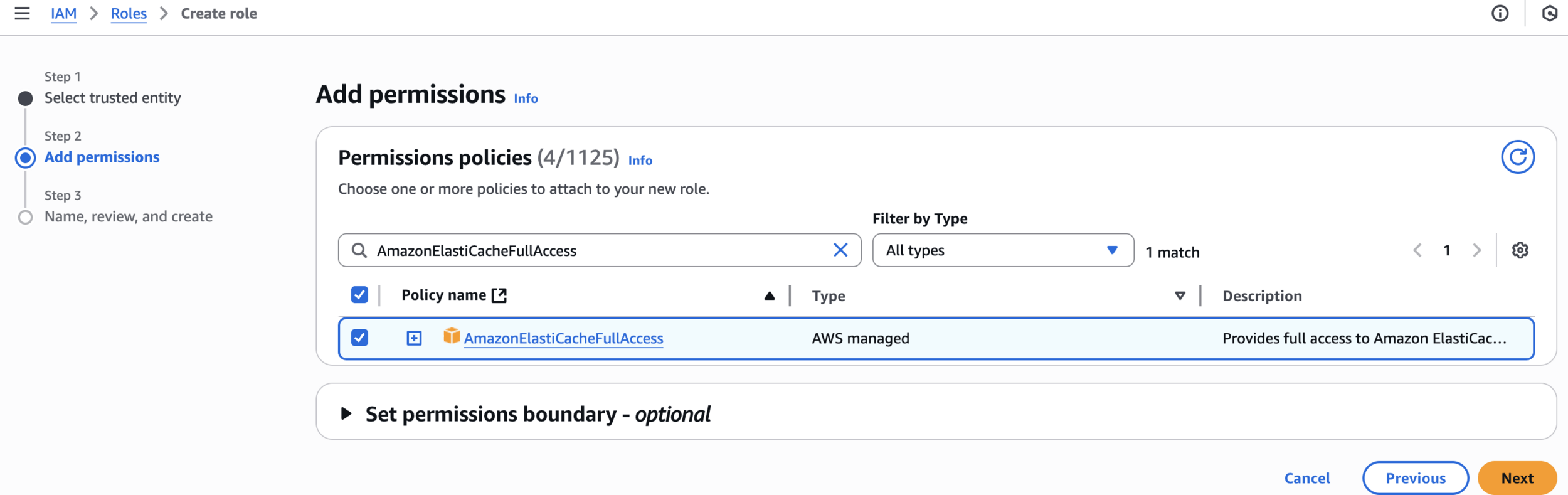
AmazonElastiCacheFullAccessAdd permissions
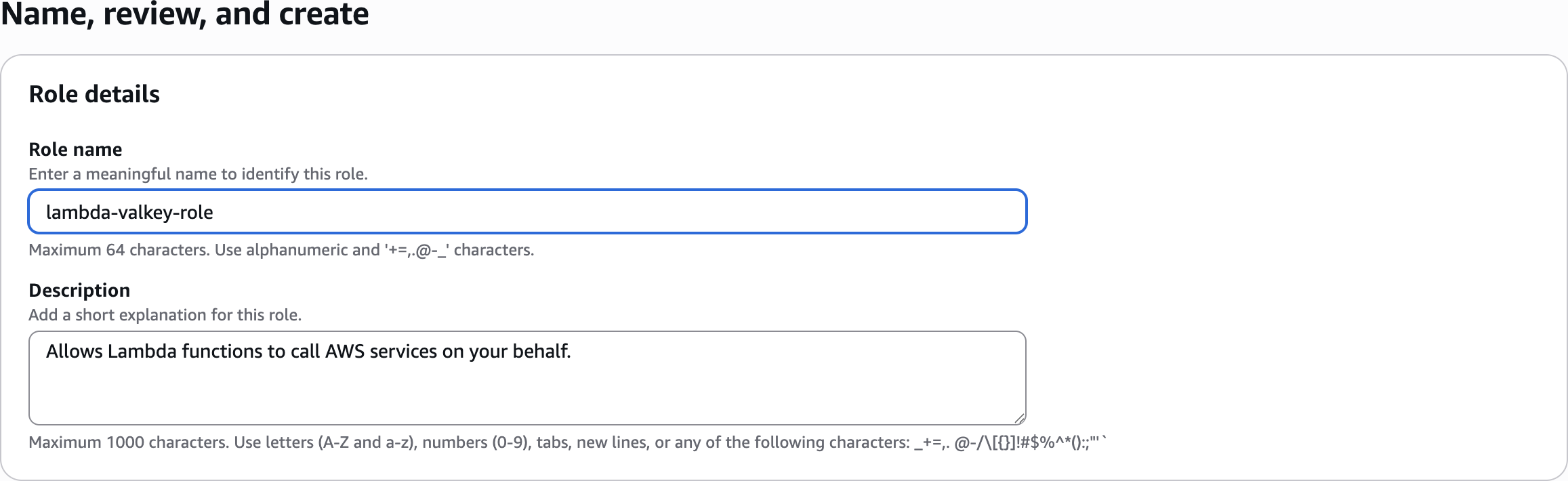
Name, review, and create
lambda-valkey-role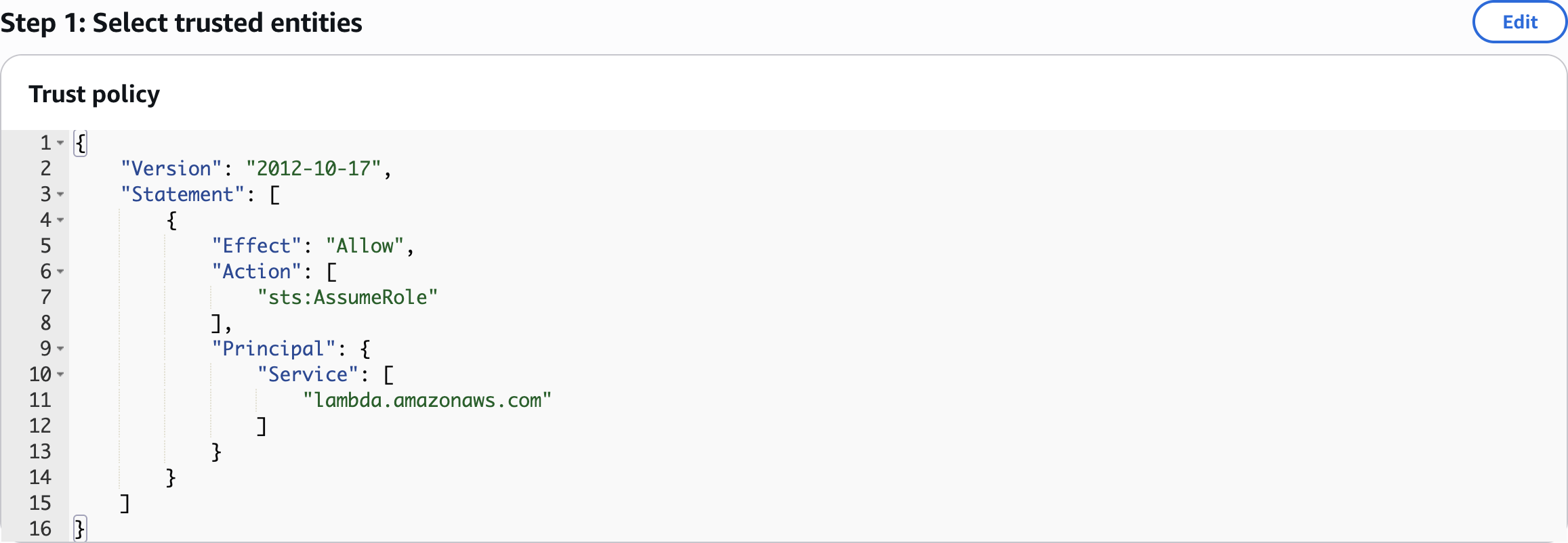
Step 1: Select trusted entities
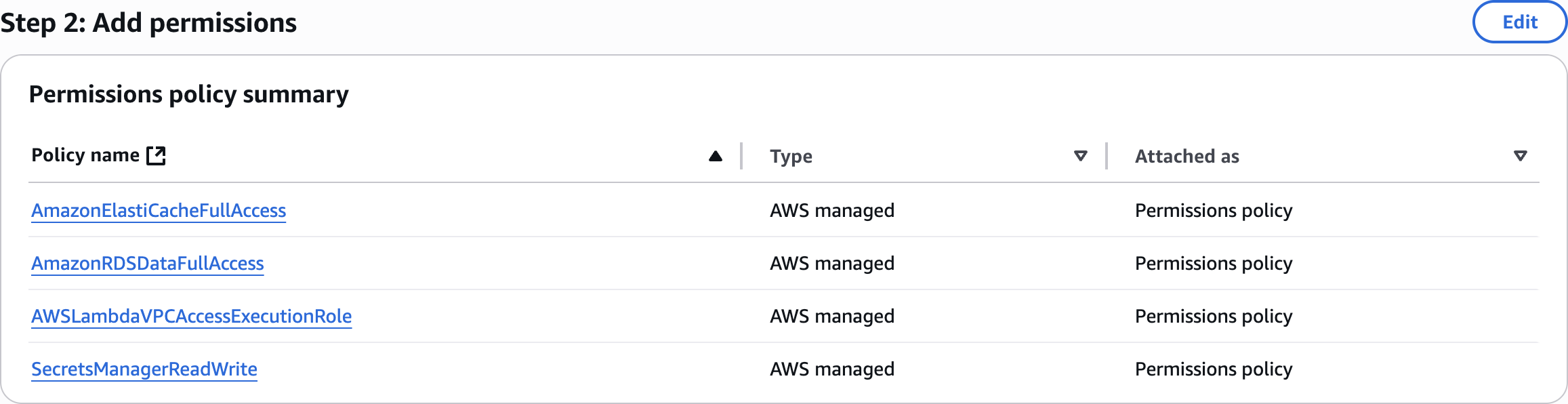
Step 2: Add permissions
Step 3: Add tags

lambda-valkey-role
Step 7: Build and Deploy Lambda Function
# Install Python 3.13 binaries
sudo yum update -y
sudo yum install -y python3.13 python3.13-pip zip
# Verify installation
python3.13 --version
pip3.13 --versionAWS CloudShell
mkdir lambda_build && cd lambda_build
cat > lambda_function.py << EOF
FILE CONTENTS
EOFpython3.13 -m pip install --target . valkey-glide boto3zip -r function.zip . -x function.zipCreate the Zip
ls -lh function.zipDownload the package from CloudShell:
- In CloudShell, click Actions → Download file
- Enter:
~/lambda_build/function.zip
~/lambda_build/function.zipDownload the zip file

Create Lambda function
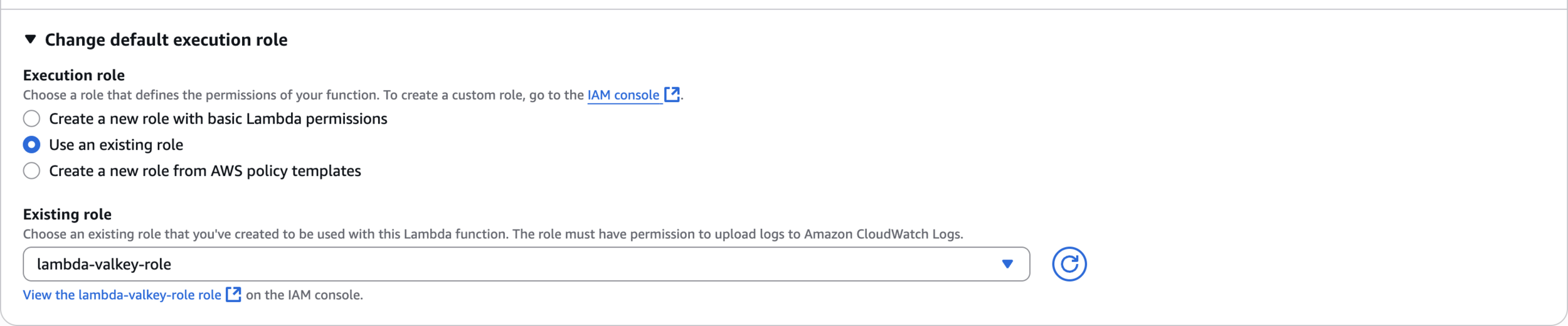
Change default execution role
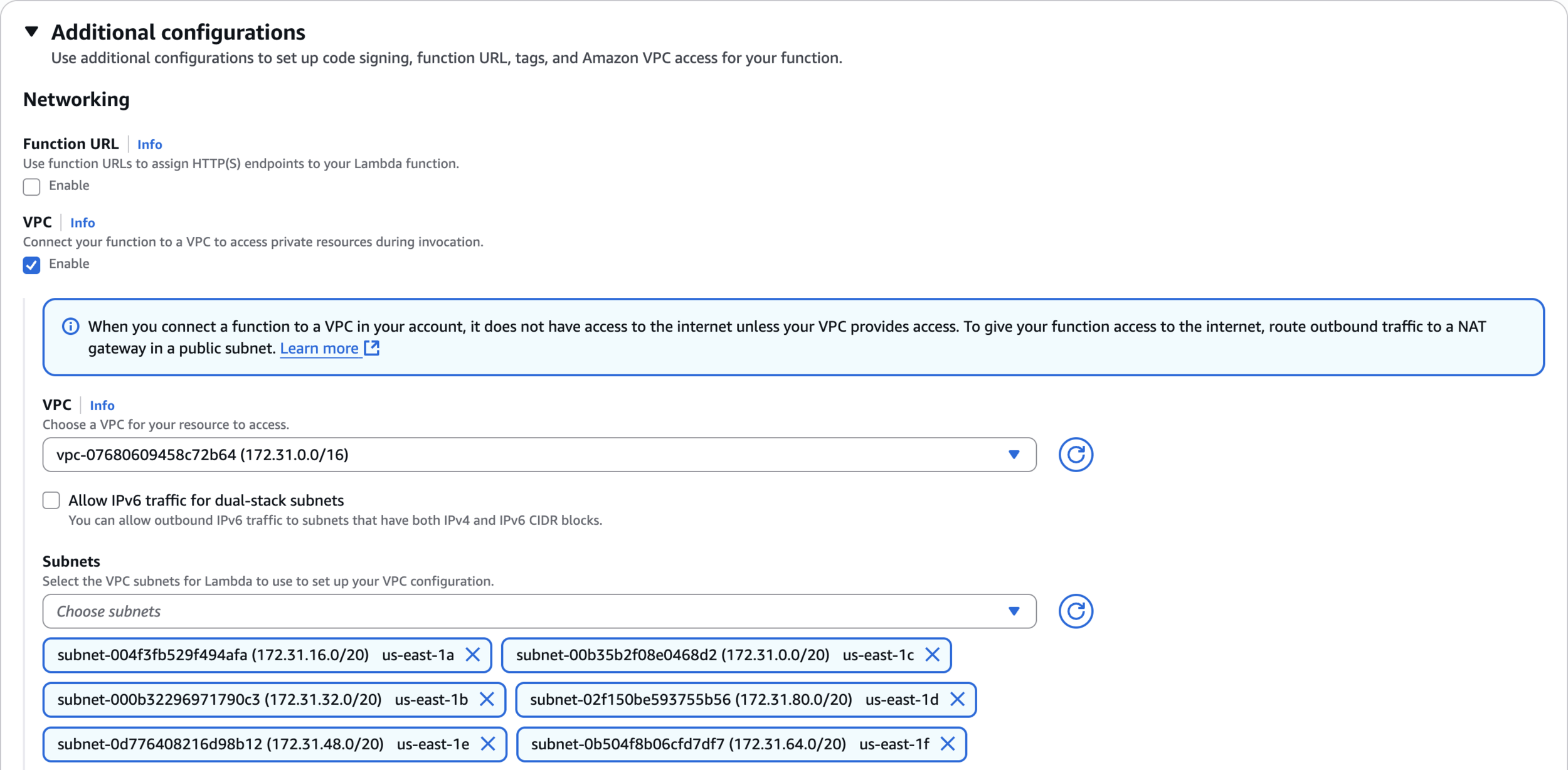
Additional configurations
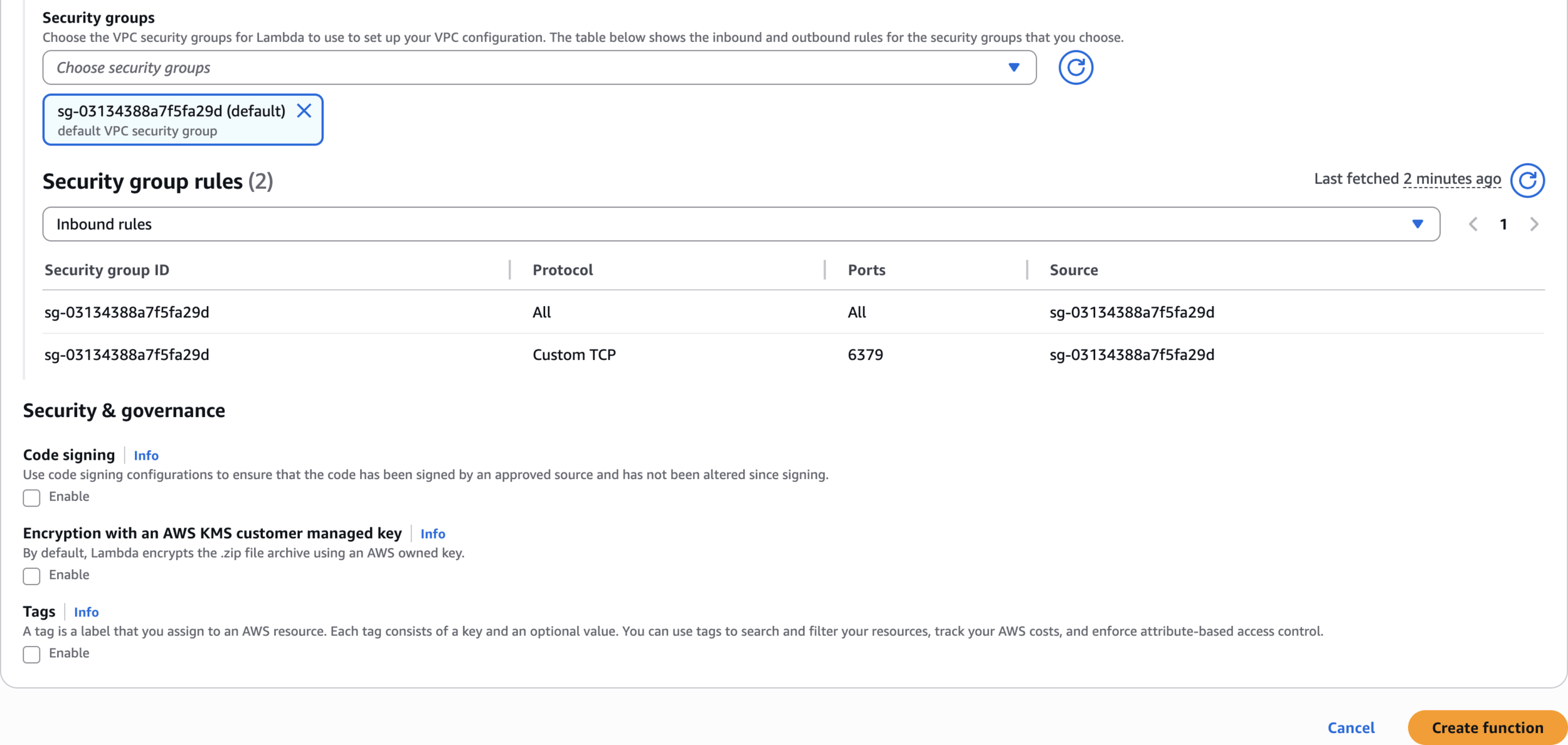
Security groups
Upload zip file
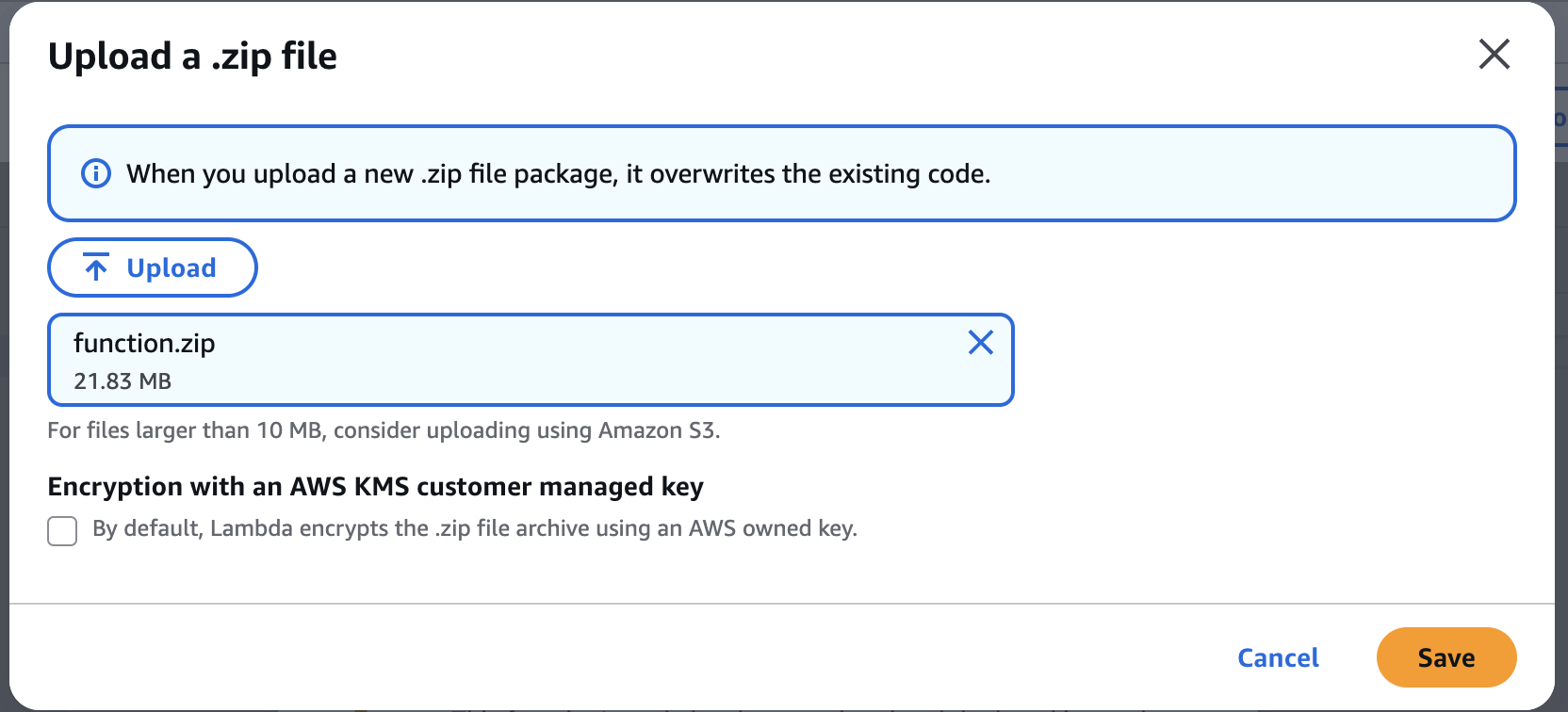
Upload a zip file
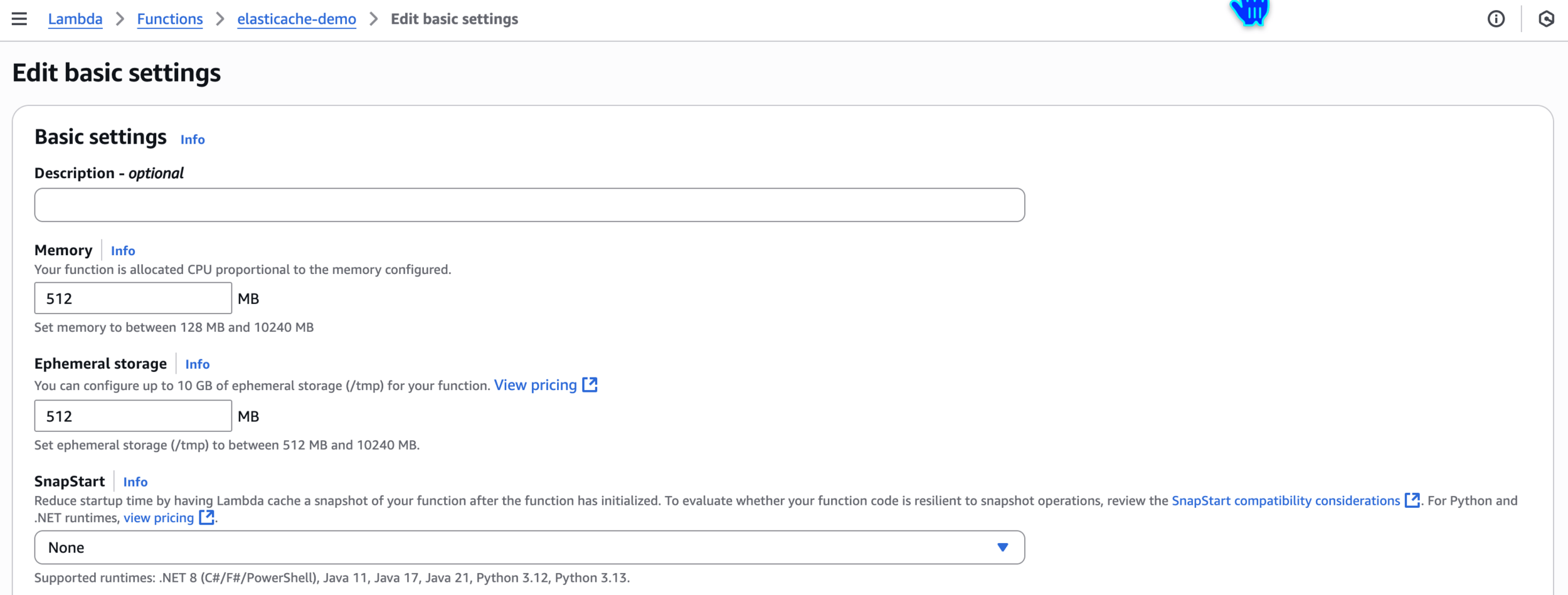
Edit basic settings
512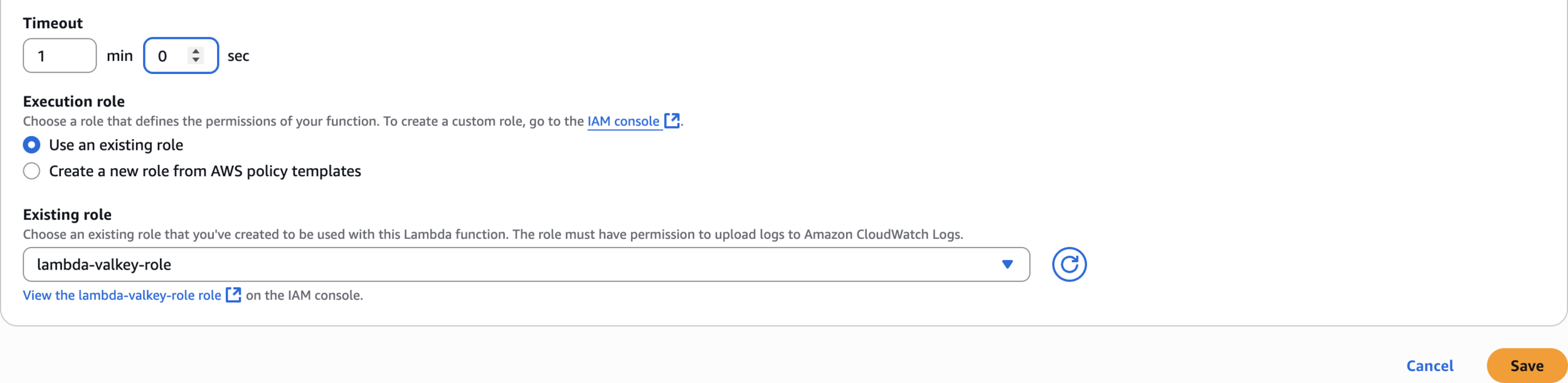
Timeout = 1 min
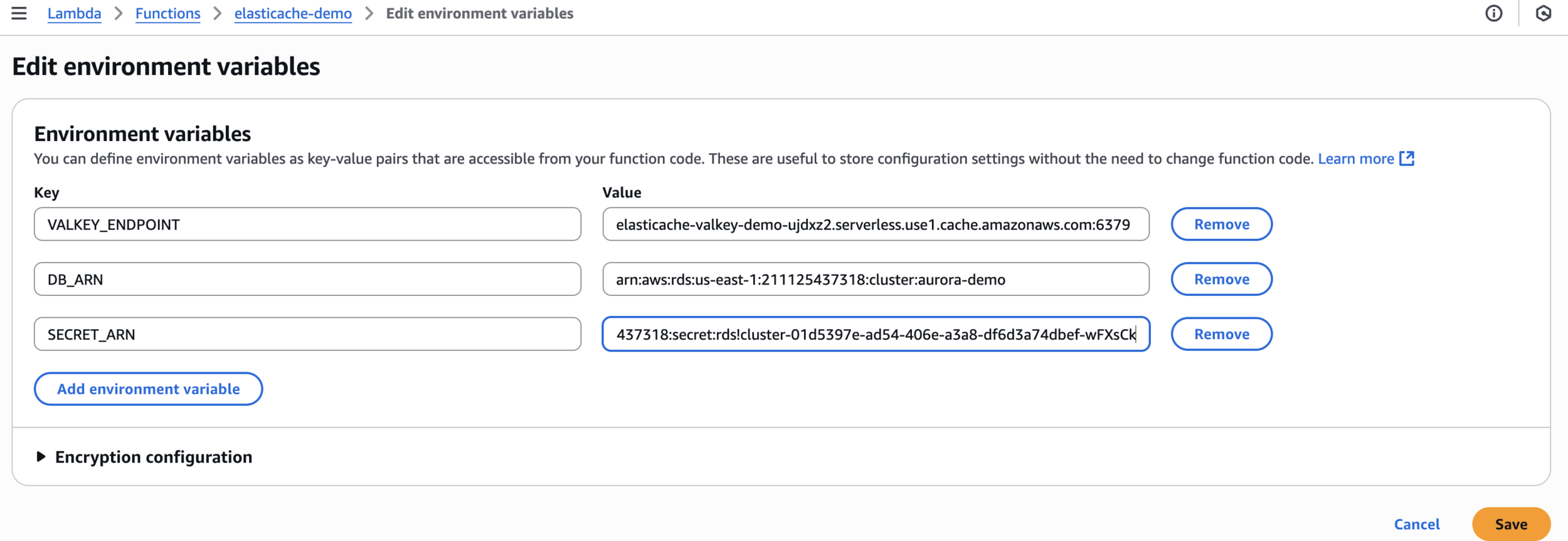
VALKEY_ENDPOINTDB_ARNSECRET_ARNEdit environment variables
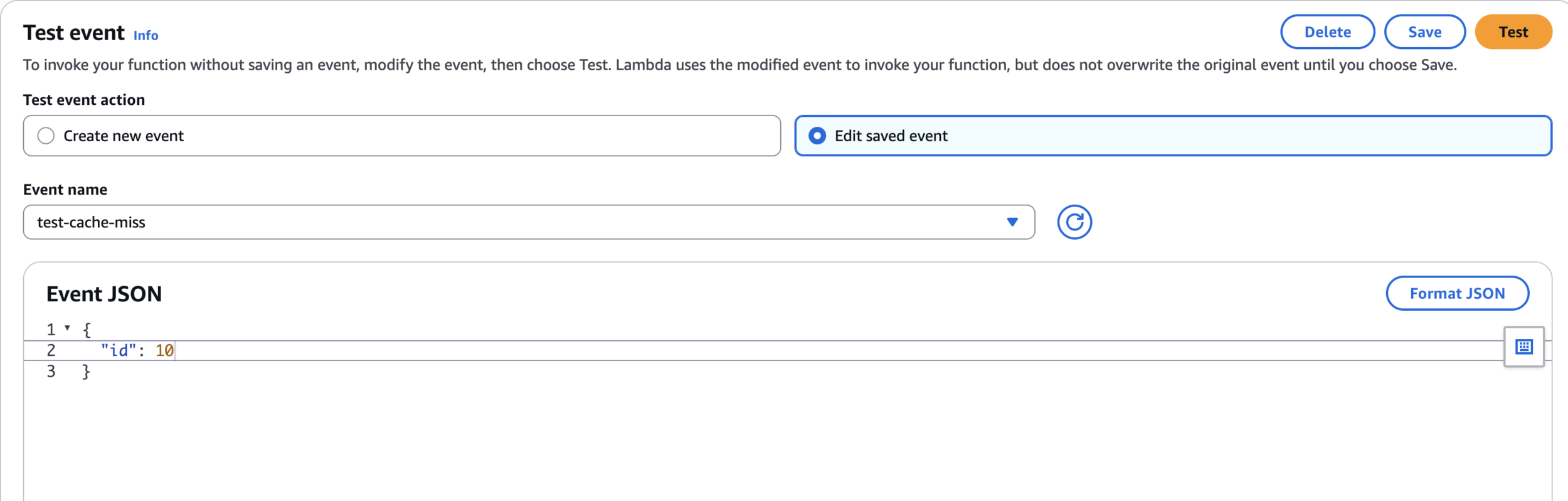
Step 8: Test the Cache-Aside Pattern
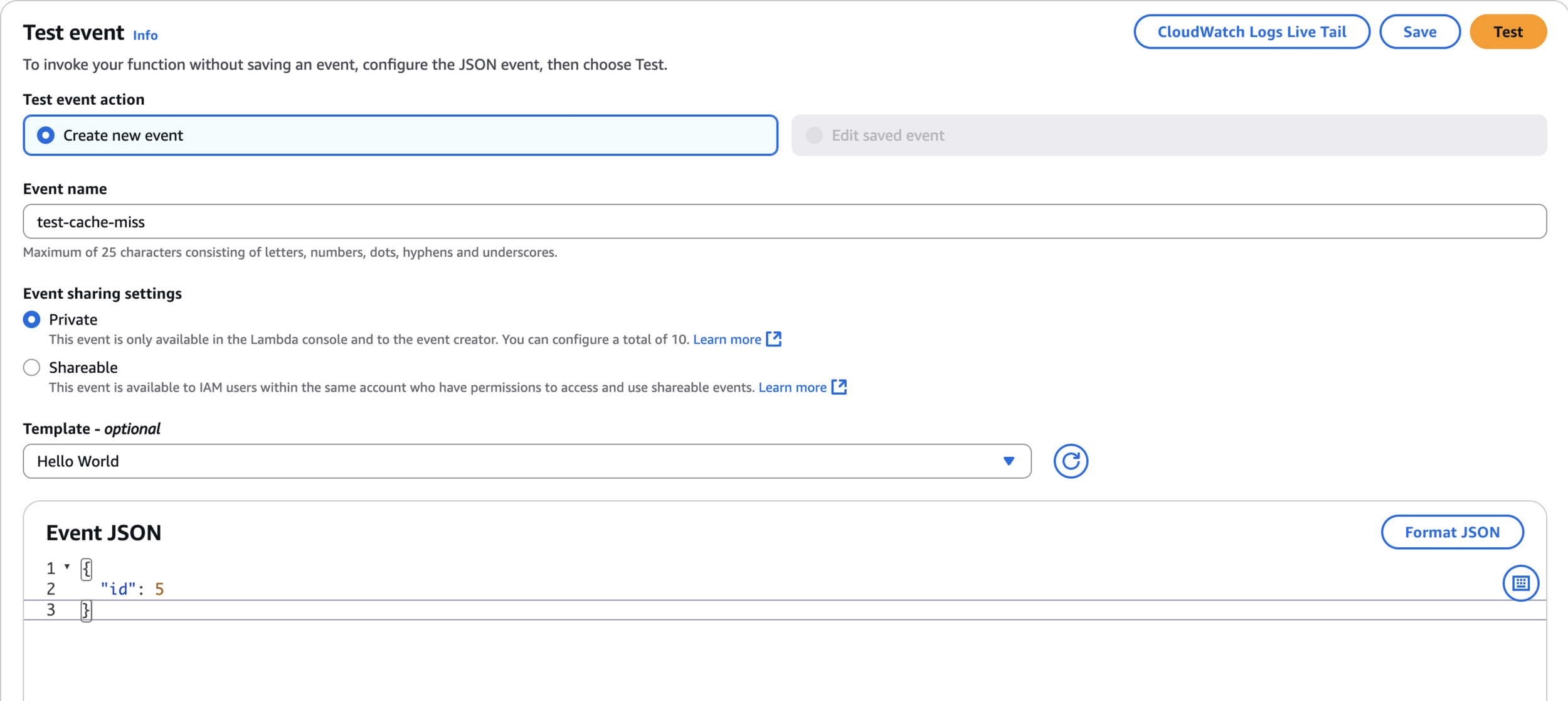
Test
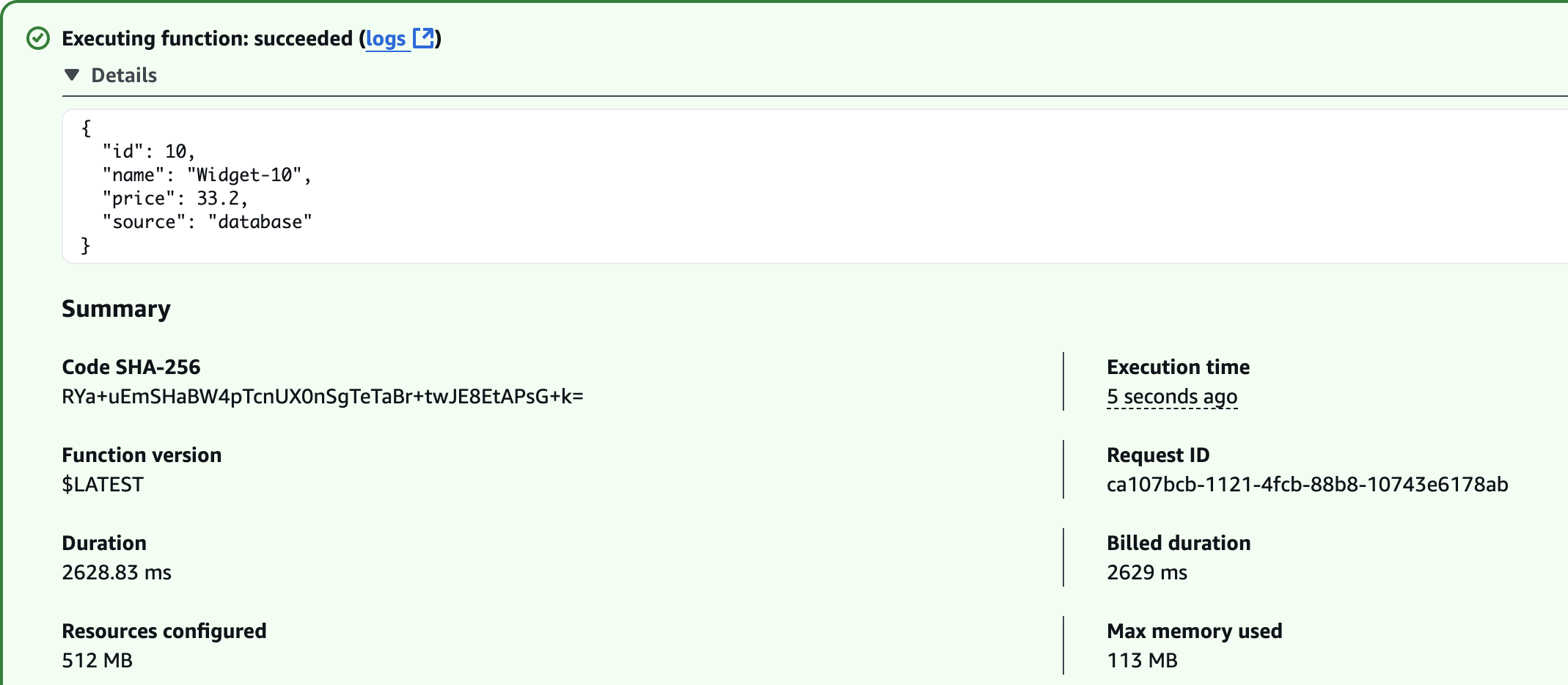
{
"id": 5
}test-cache-miss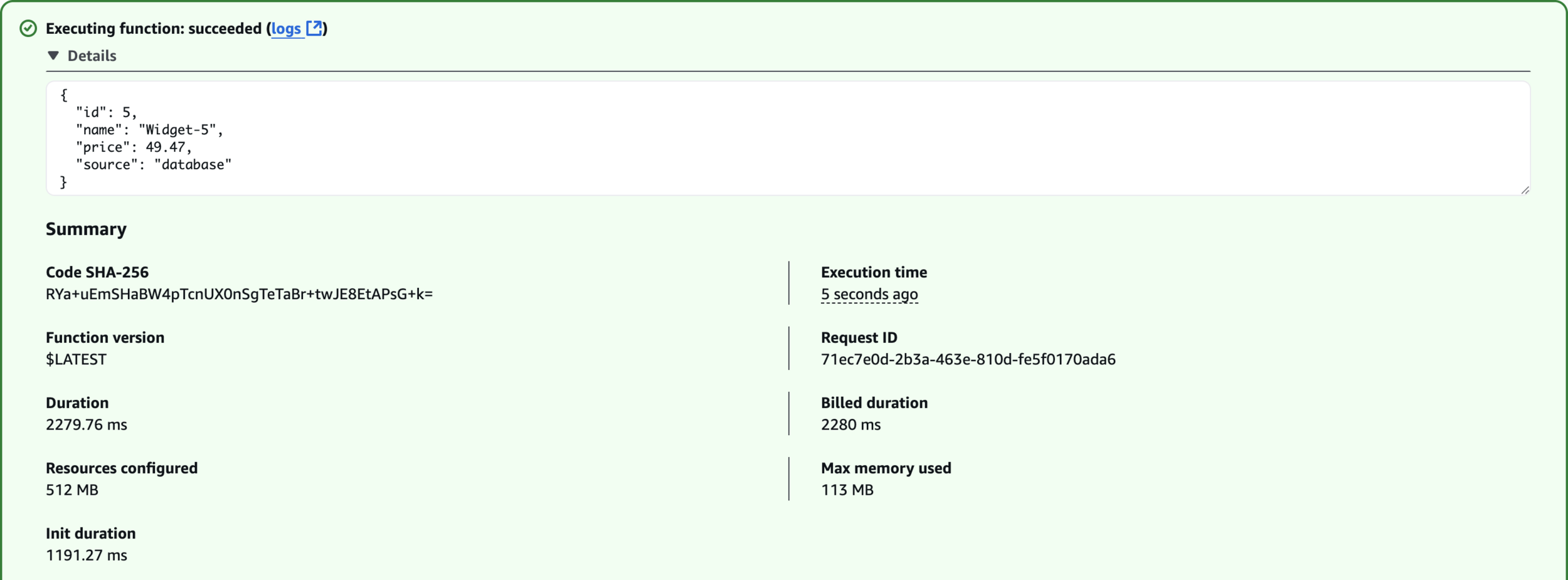
Fetched from Database
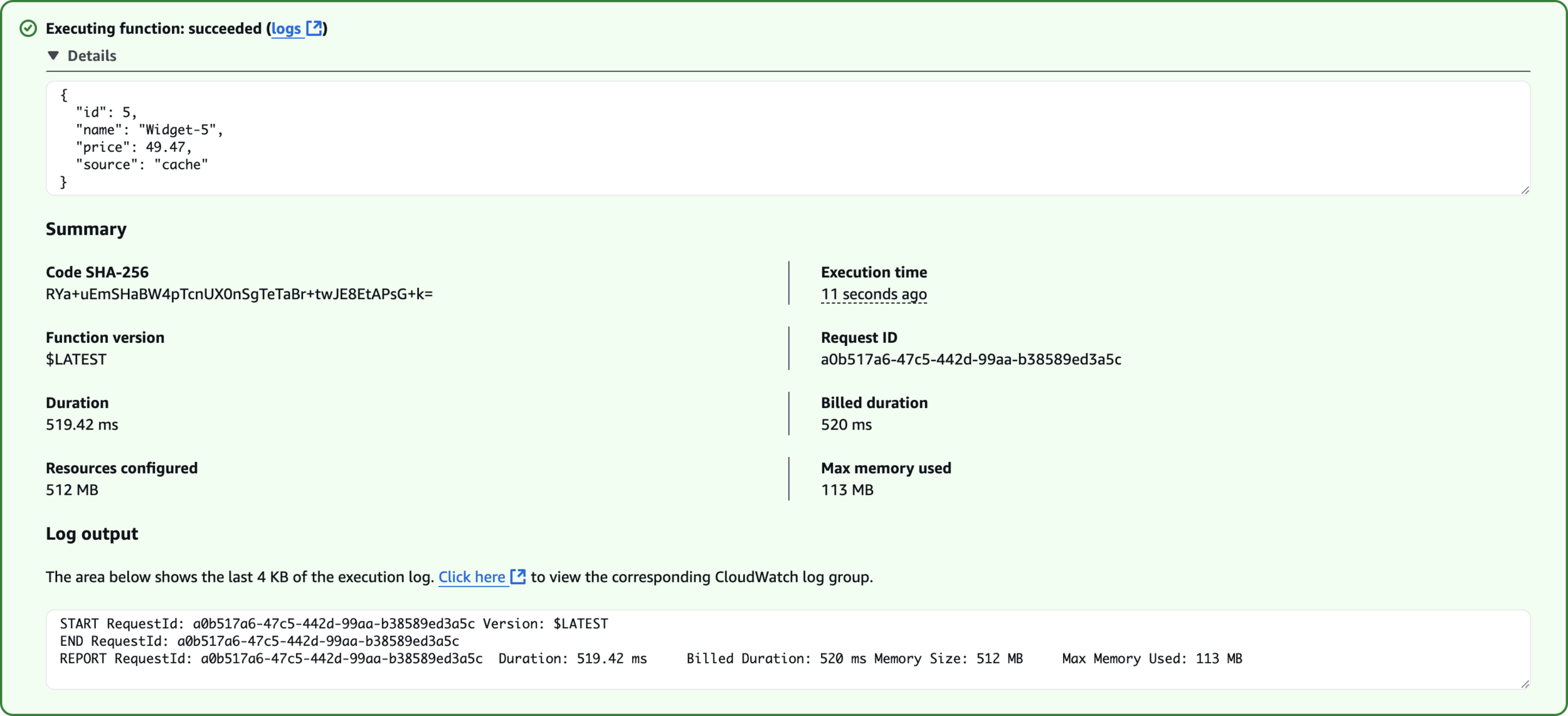
Fetched from Cache

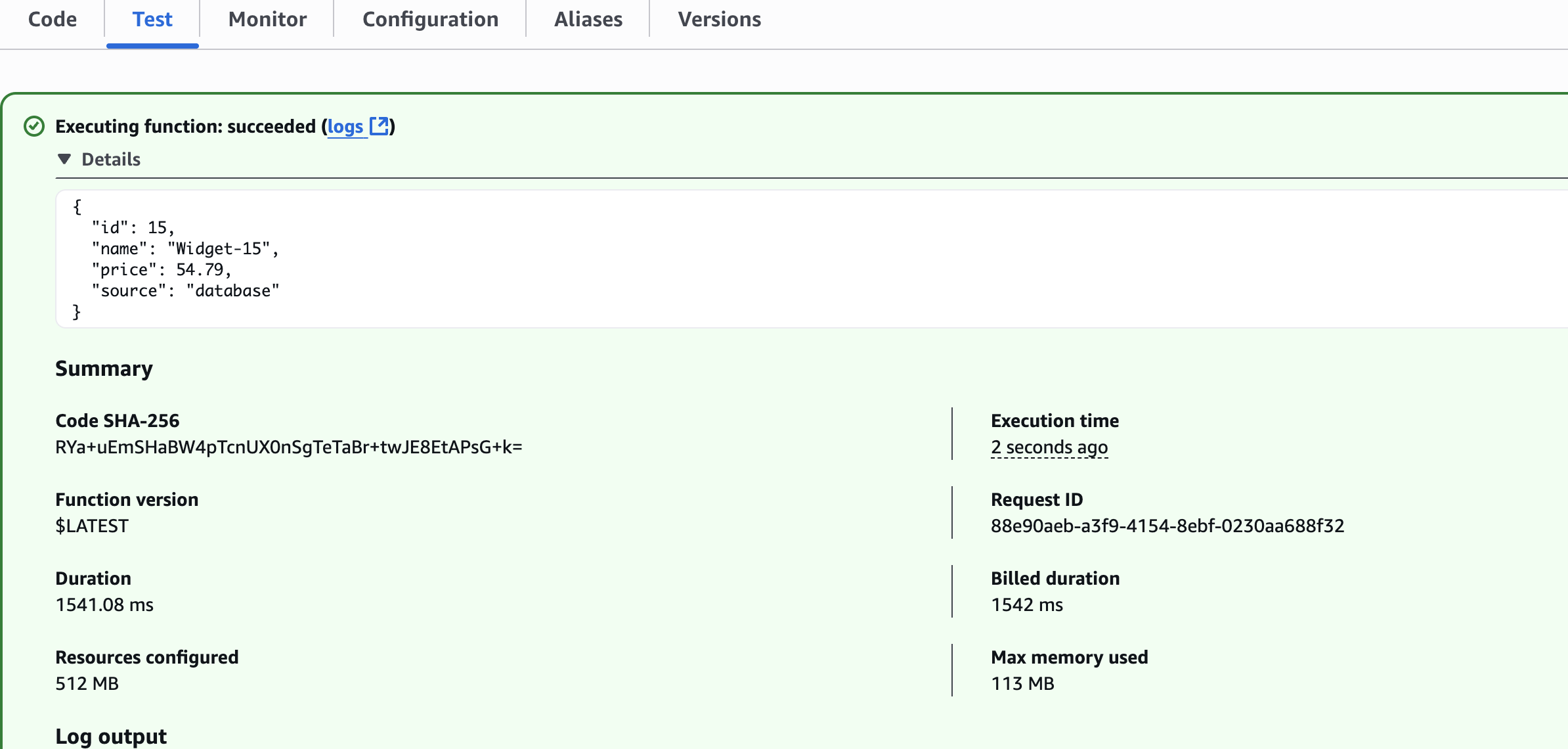
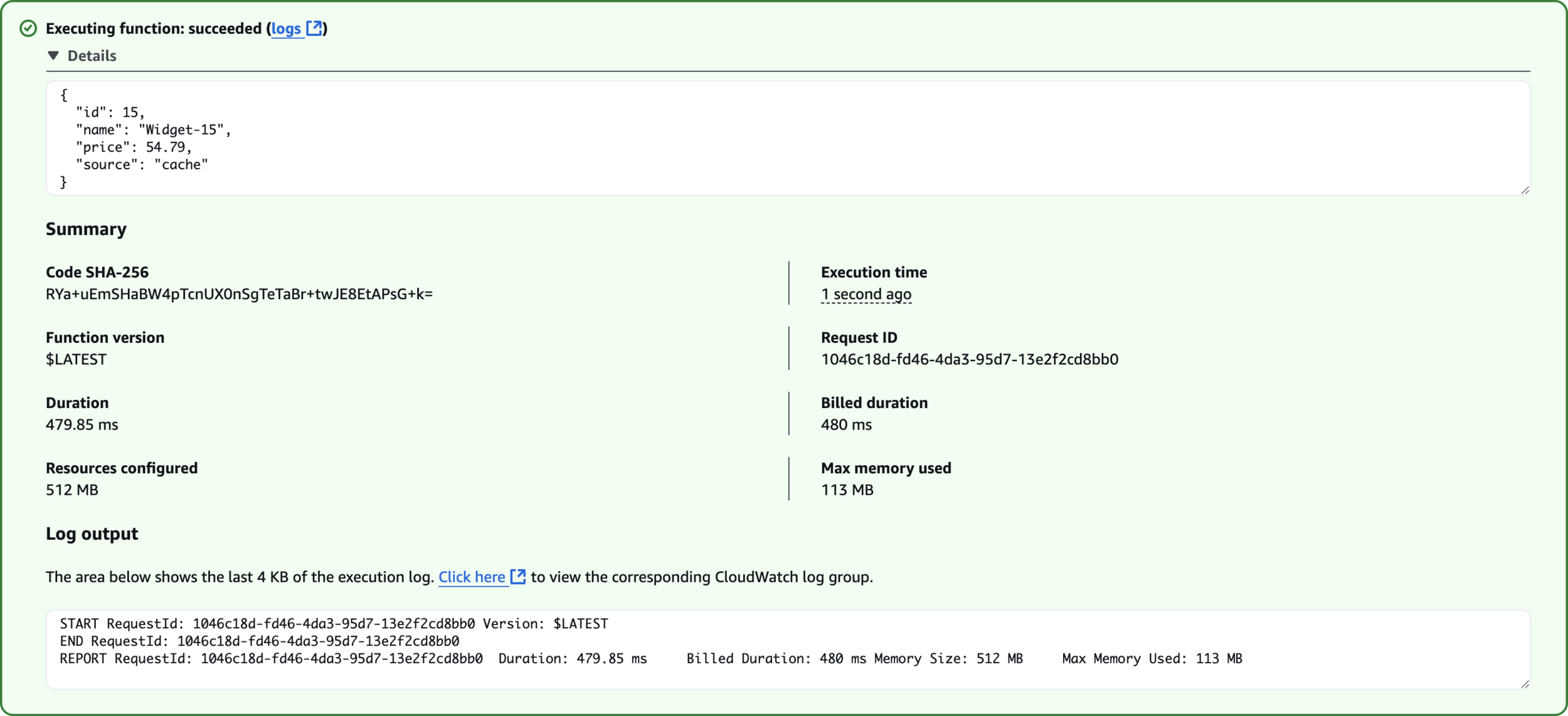
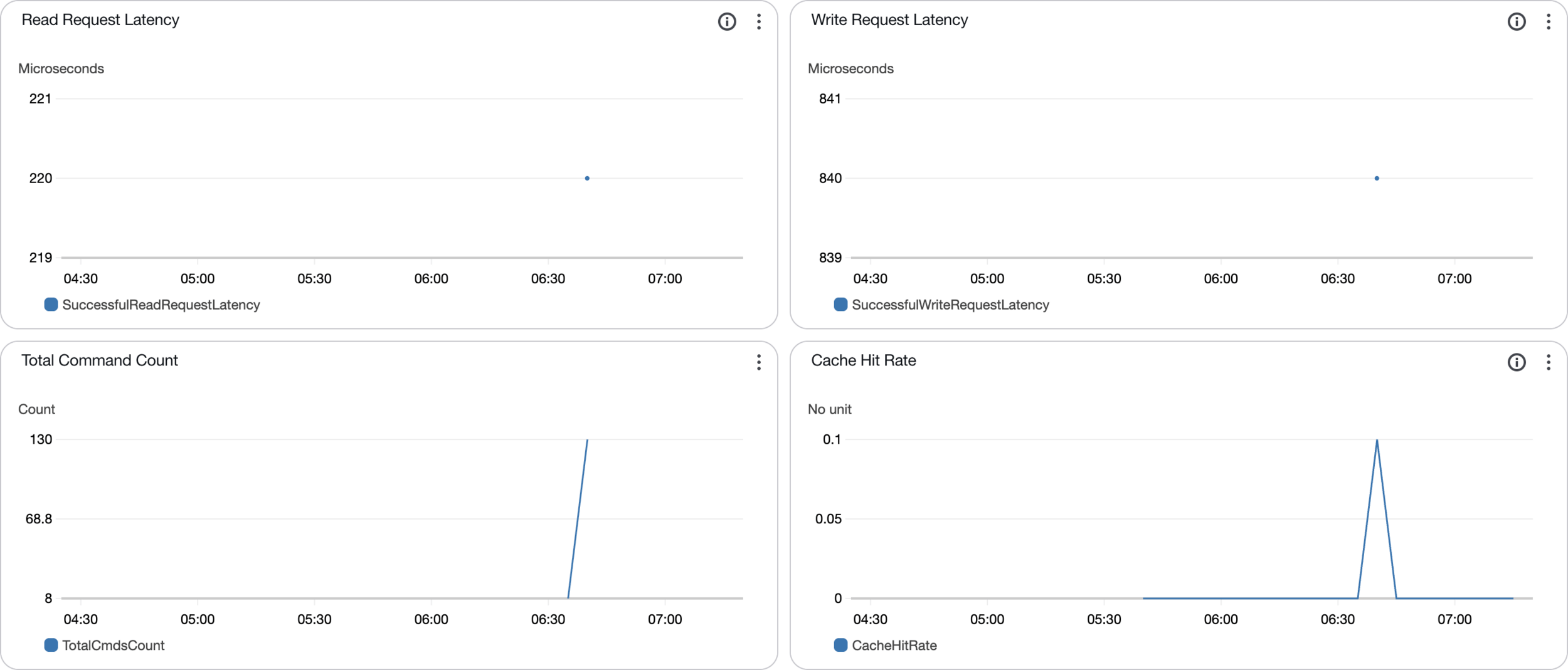
Elasticache Monitoring
Clean Up
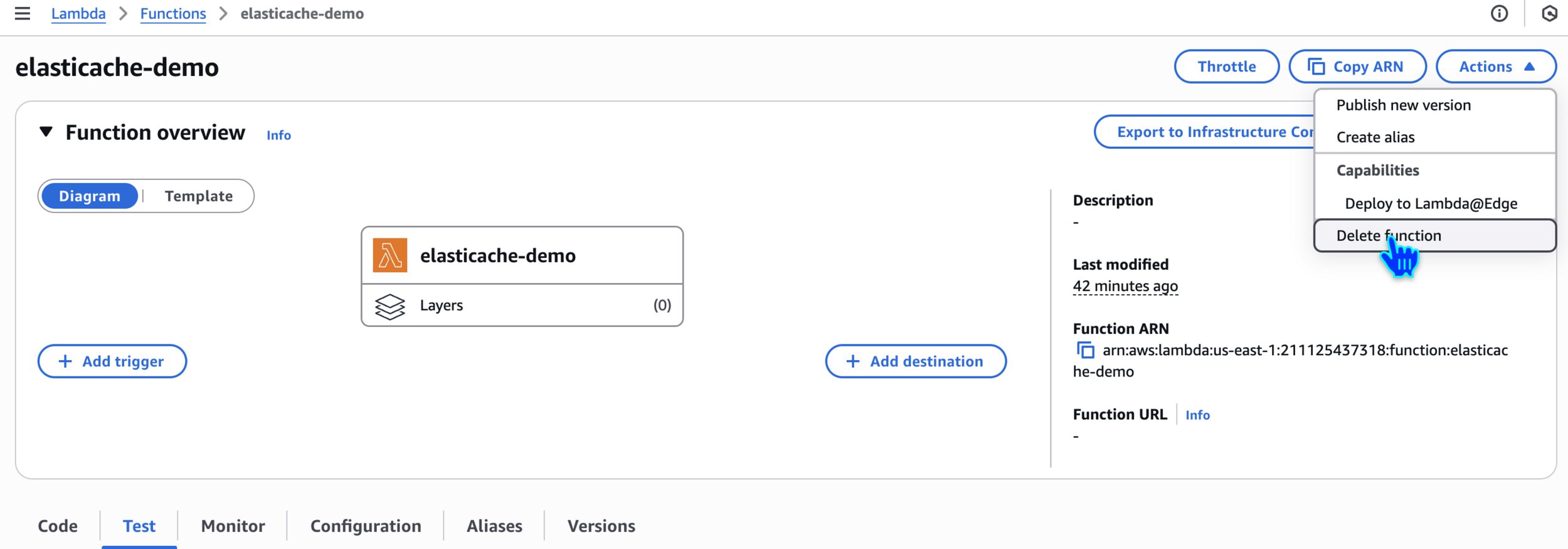
Delete Lambda Function
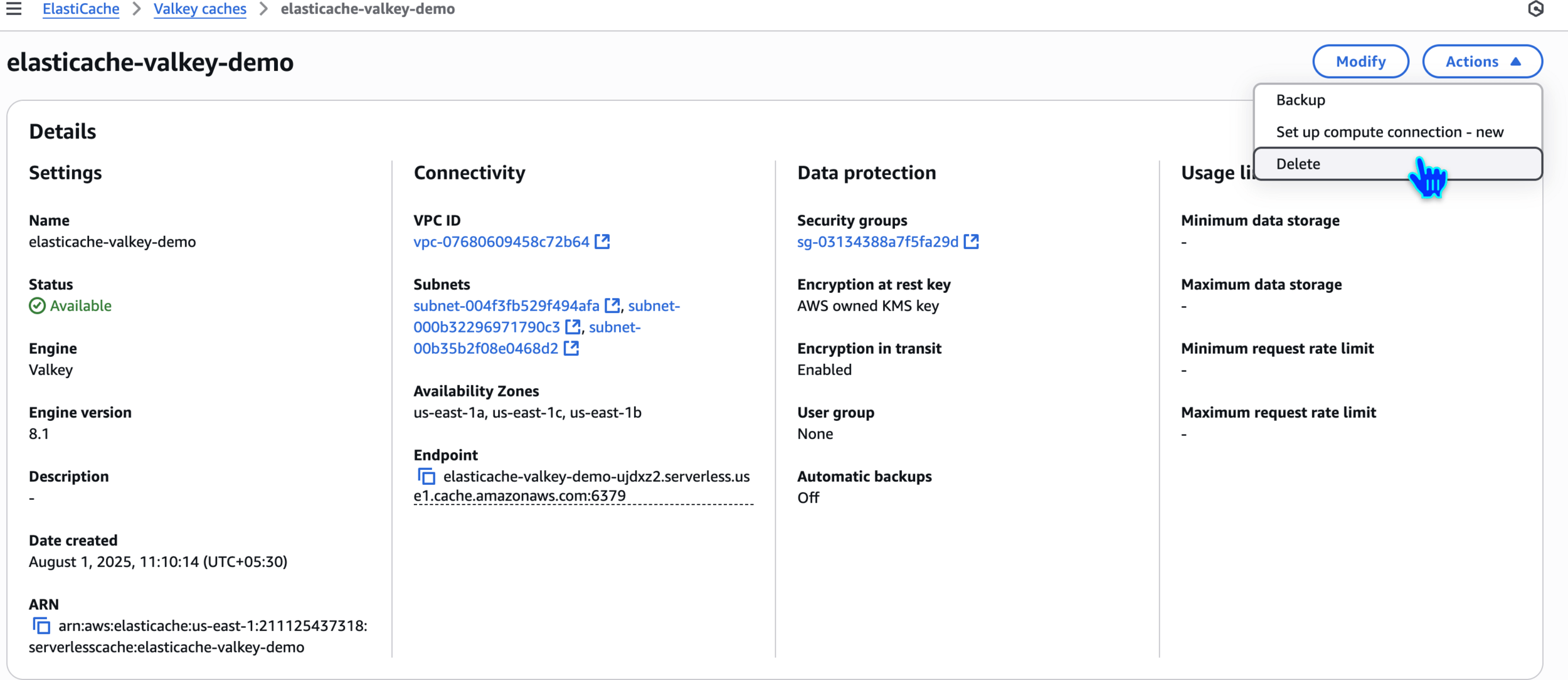
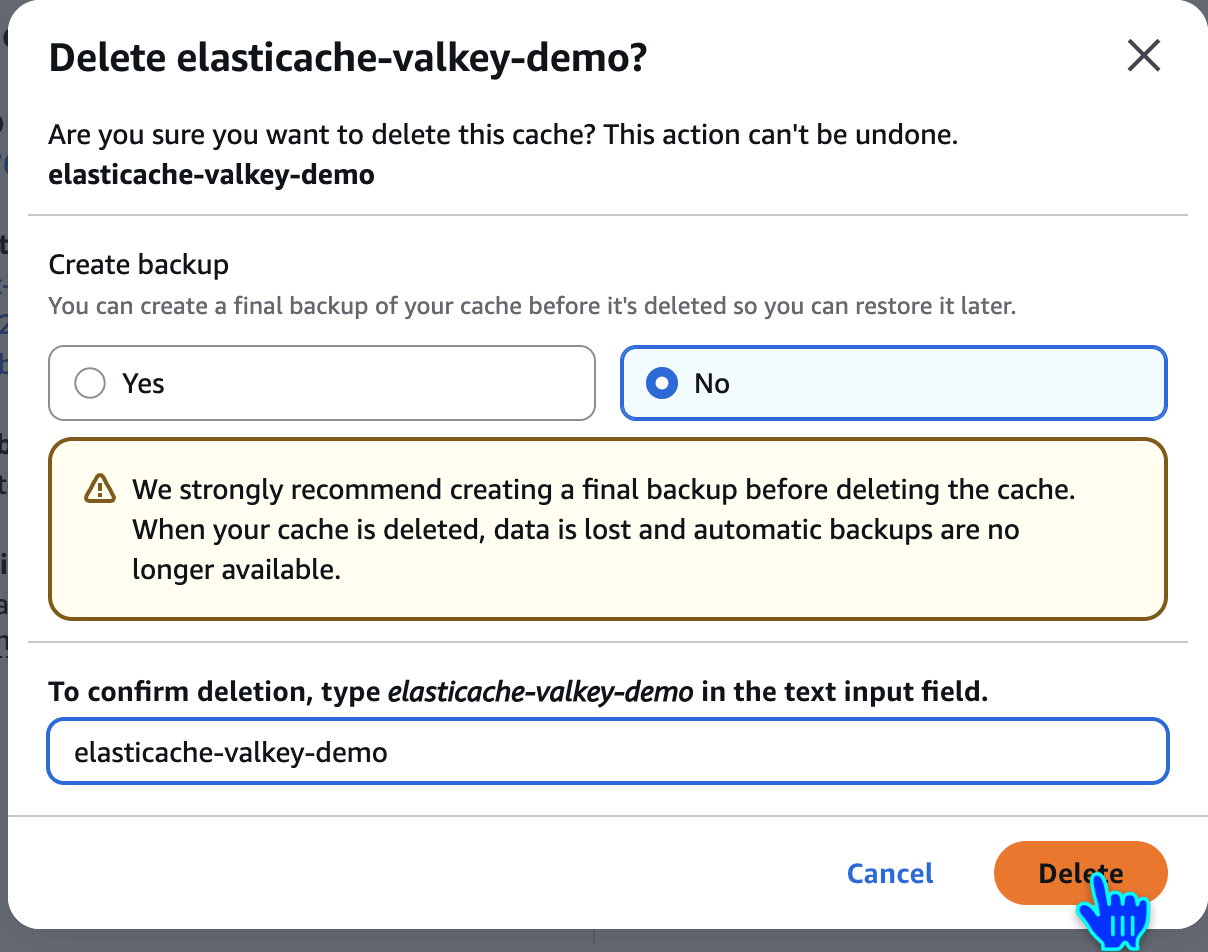
Delete Elasticache Valkey Cache
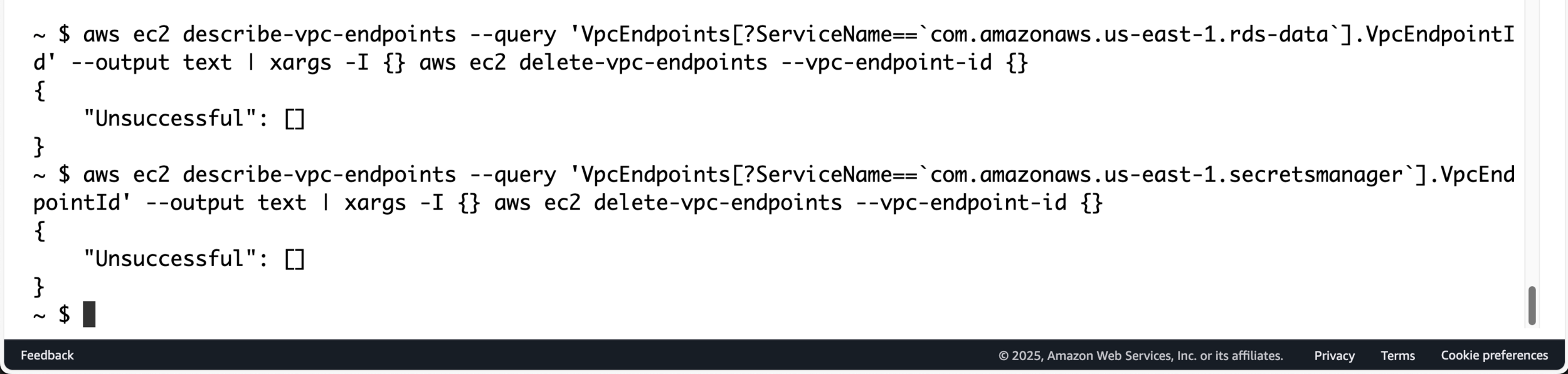
Delete VPC Endpoints
# List and delete VPC endpoints
aws ec2 describe-vpc-endpoints \
--query 'VpcEndpoints[?ServiceName==`com.amazonaws.us-east-1.rds-data`].VpcEndpointId' \
--output text | xargs -I {} aws ec2 delete-vpc-endpoints --vpc-endpoint-id {}aws ec2 describe-vpc-endpoints \
--query 'VpcEndpoints[?ServiceName==`com.amazonaws.us-east-1.secretsmanager`].VpcEndpointId' \
--output text | xargs -I {} aws ec2 delete-vpc-endpoints --vpc-endpoint-id {}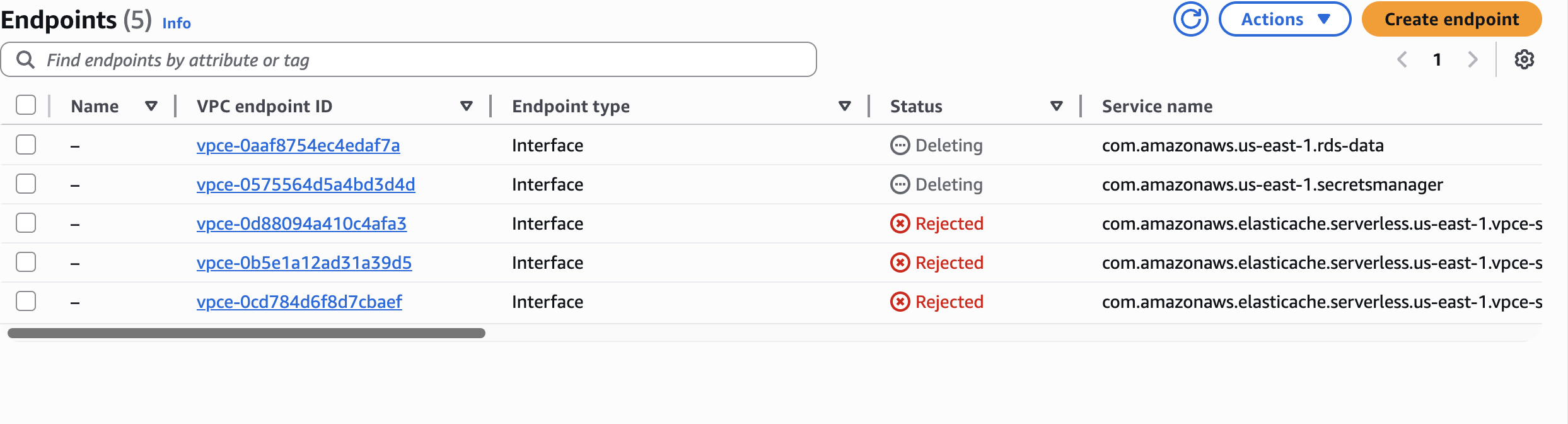
Endpoints
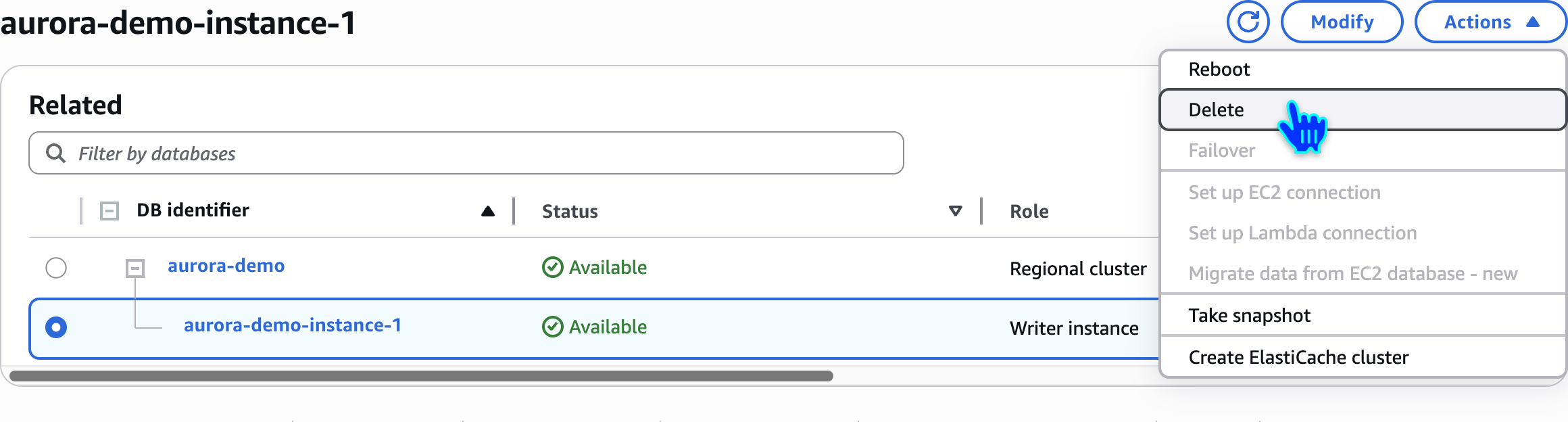
Delete Aurora Database Instance
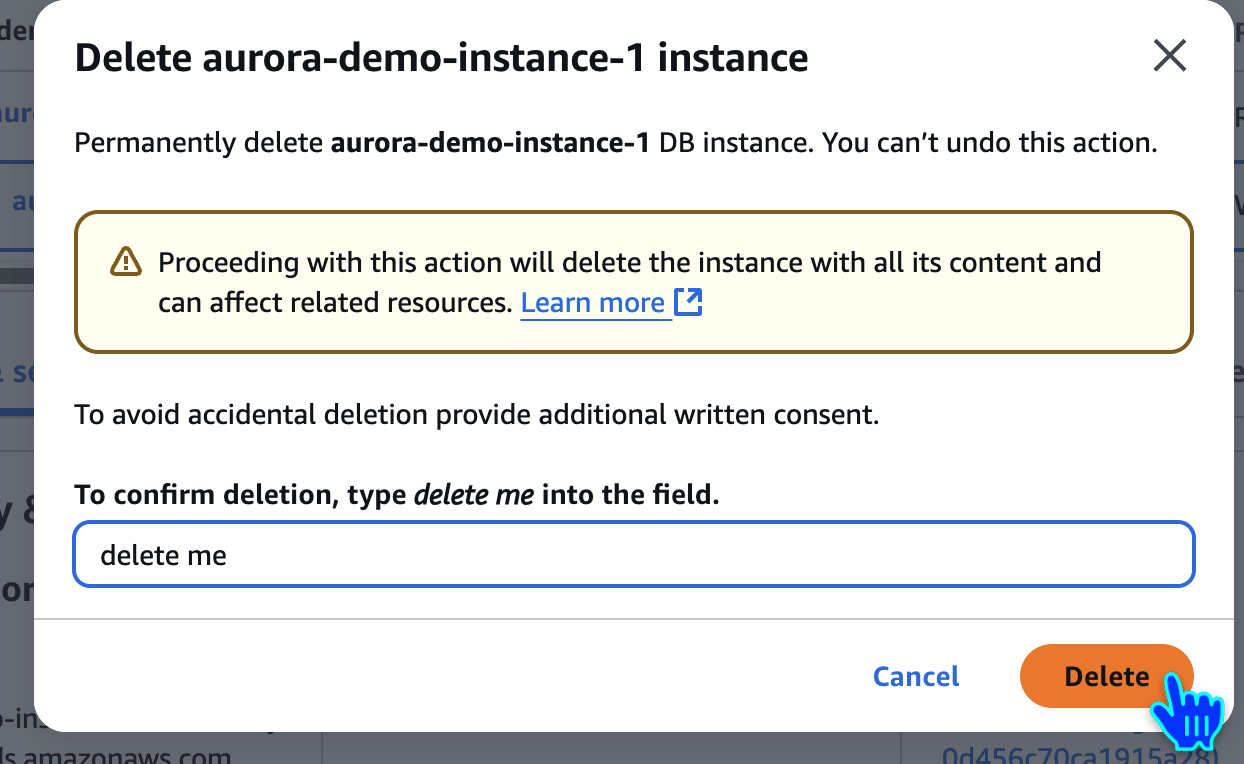
delete me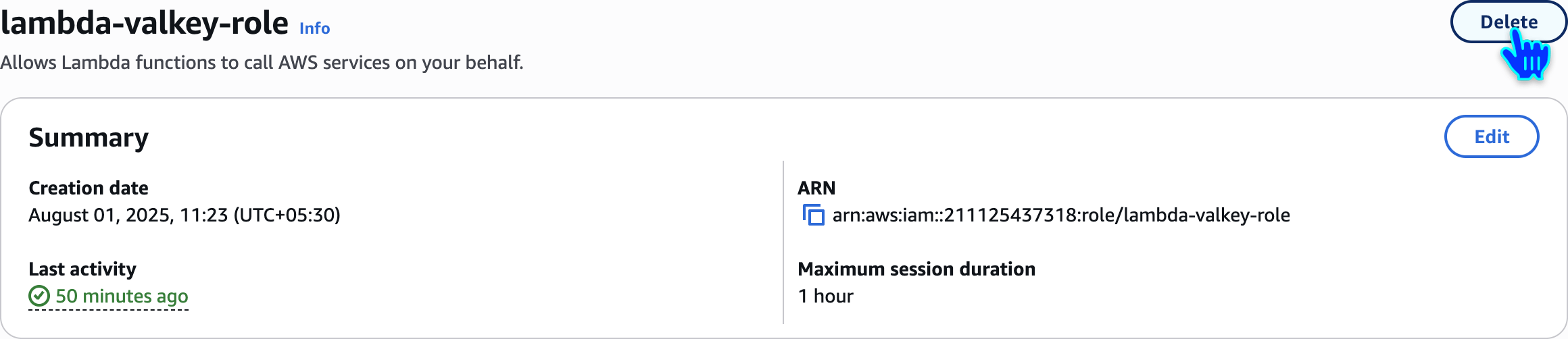
Delete Lambda Execution Role
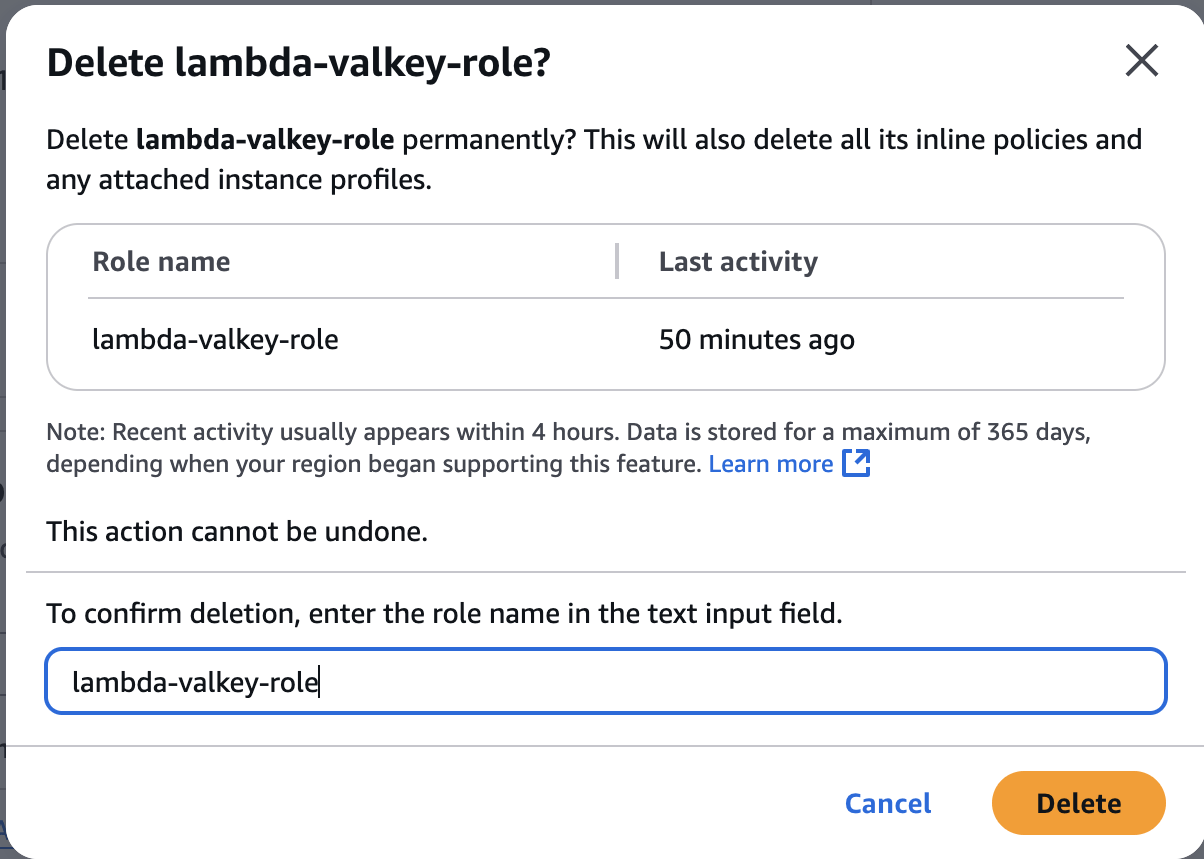
lambda-valkey-role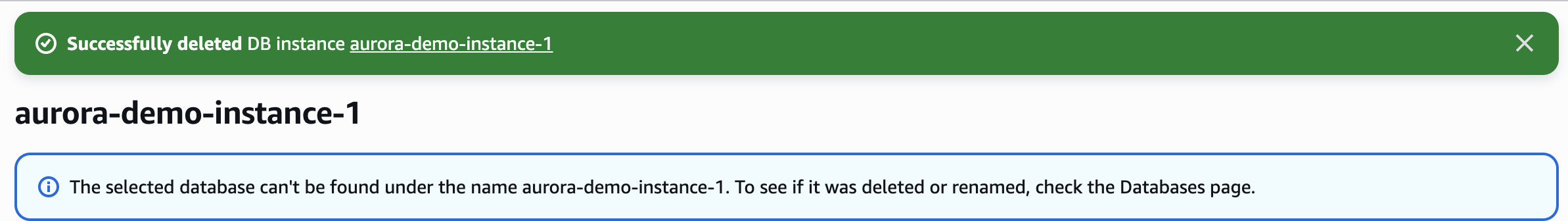
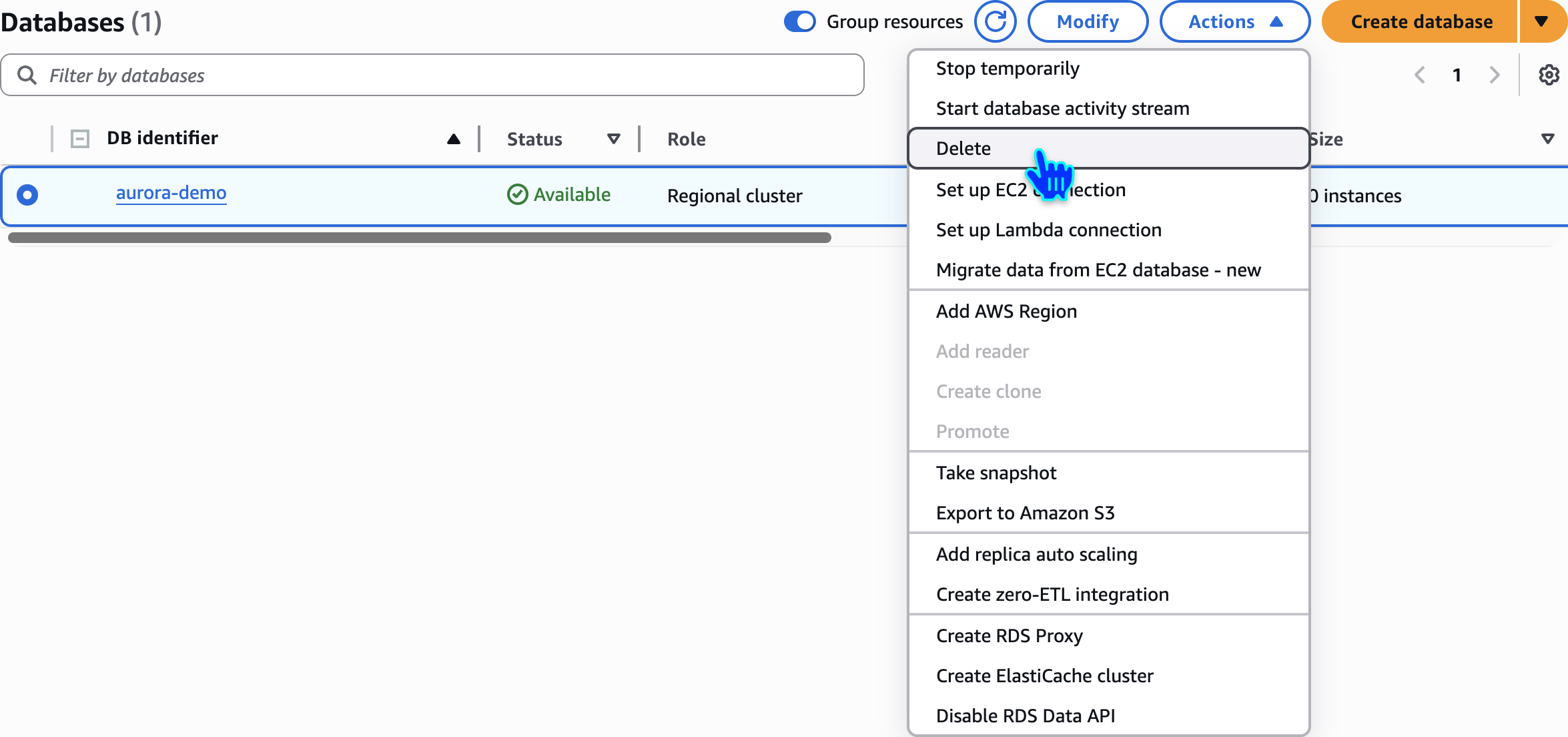
Delete Aurora Database
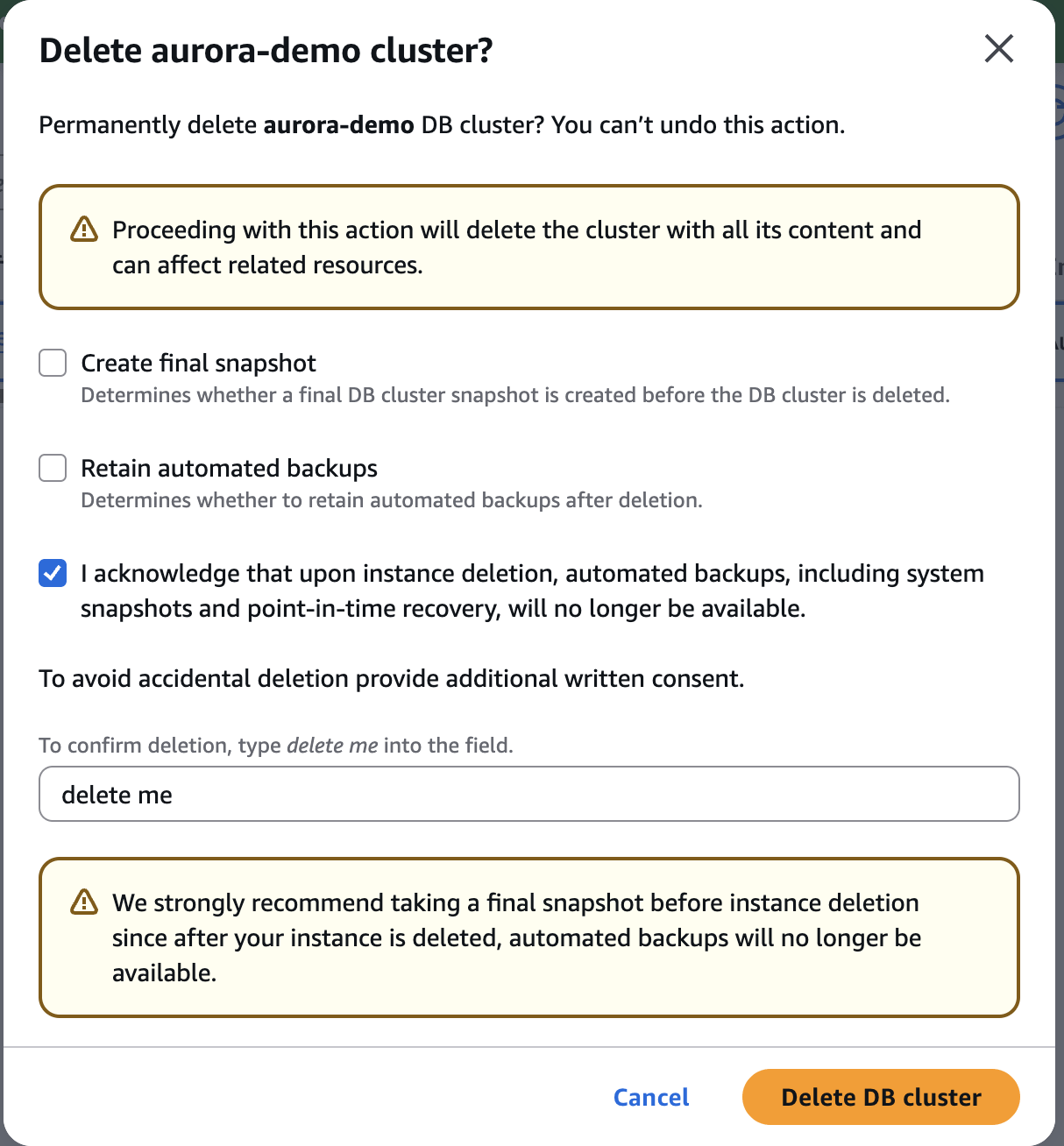
delete me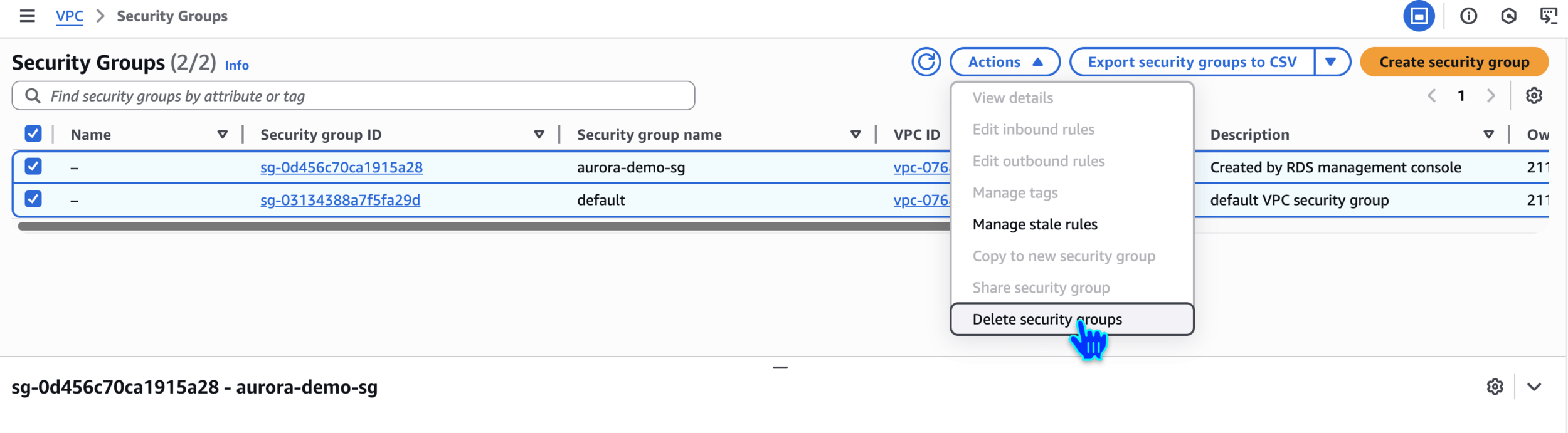
Delete Security Groups
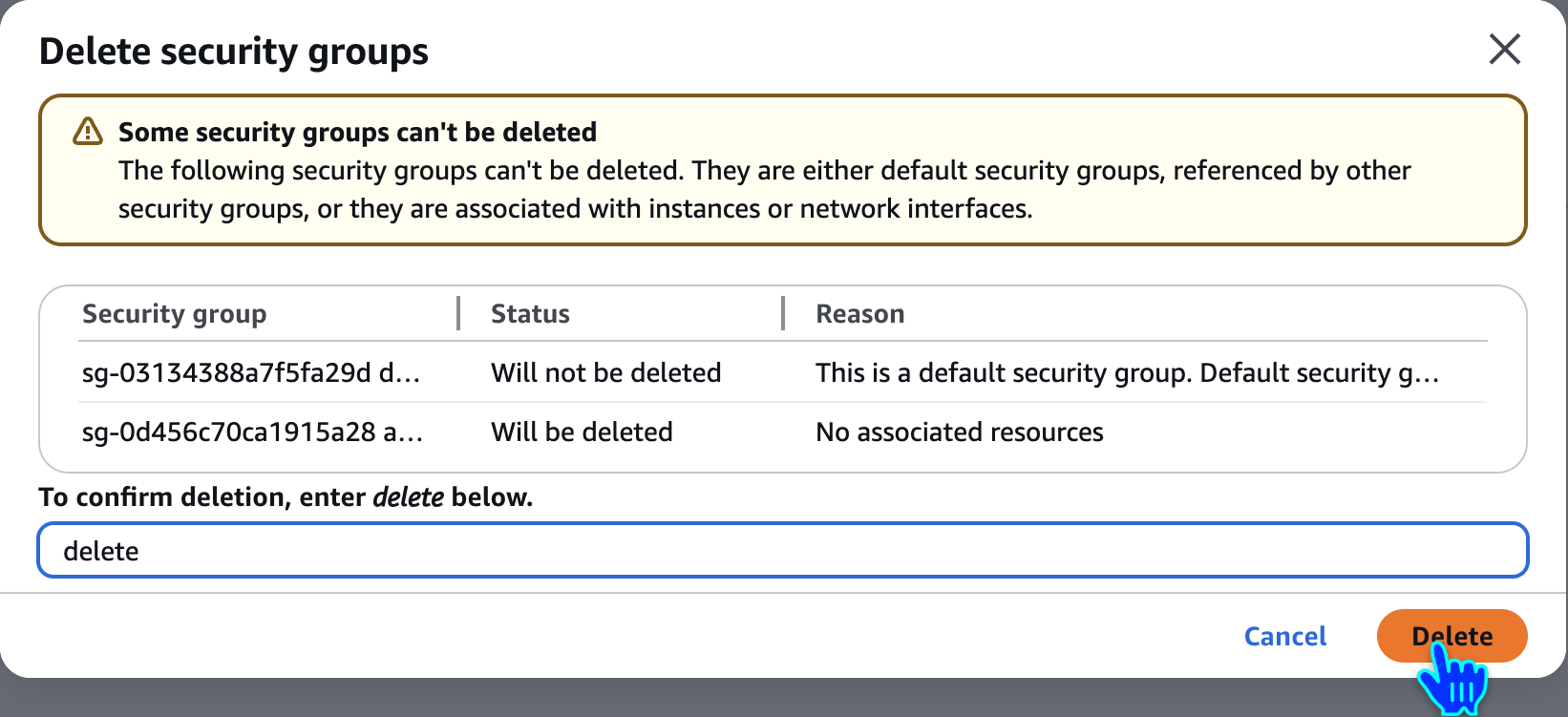
delete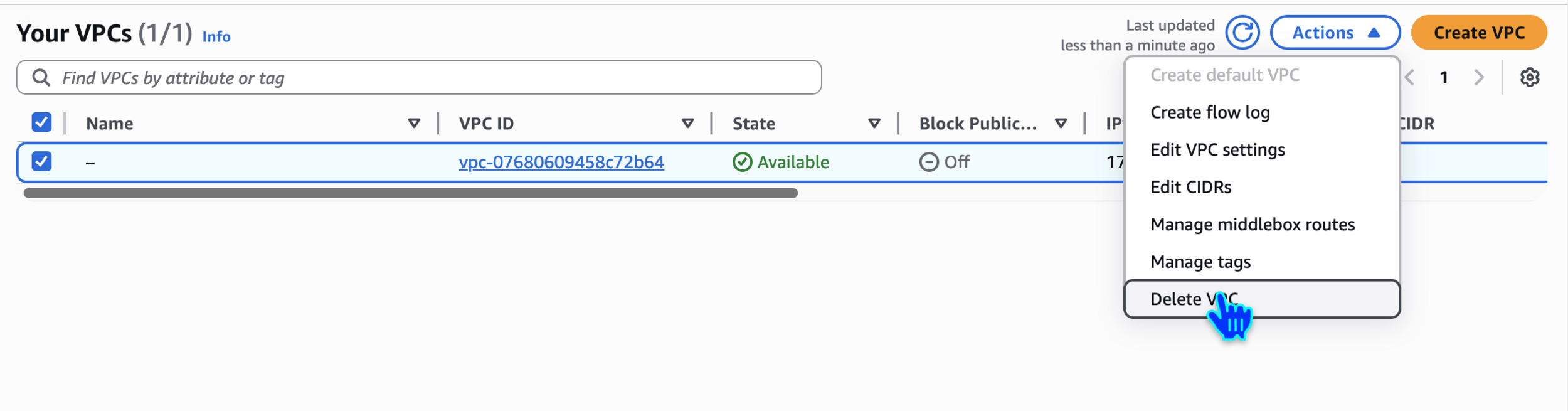
Optional - Delete VPC
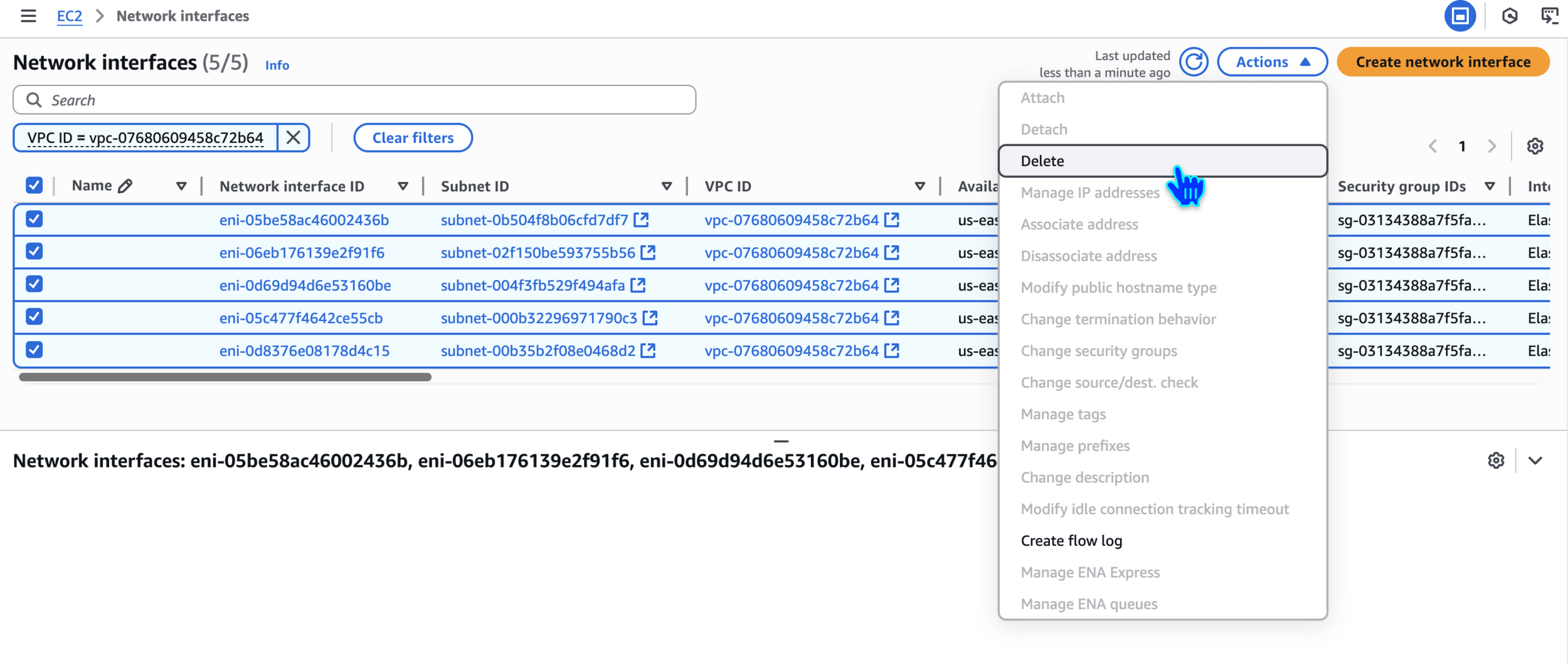
Delete Network interfaces
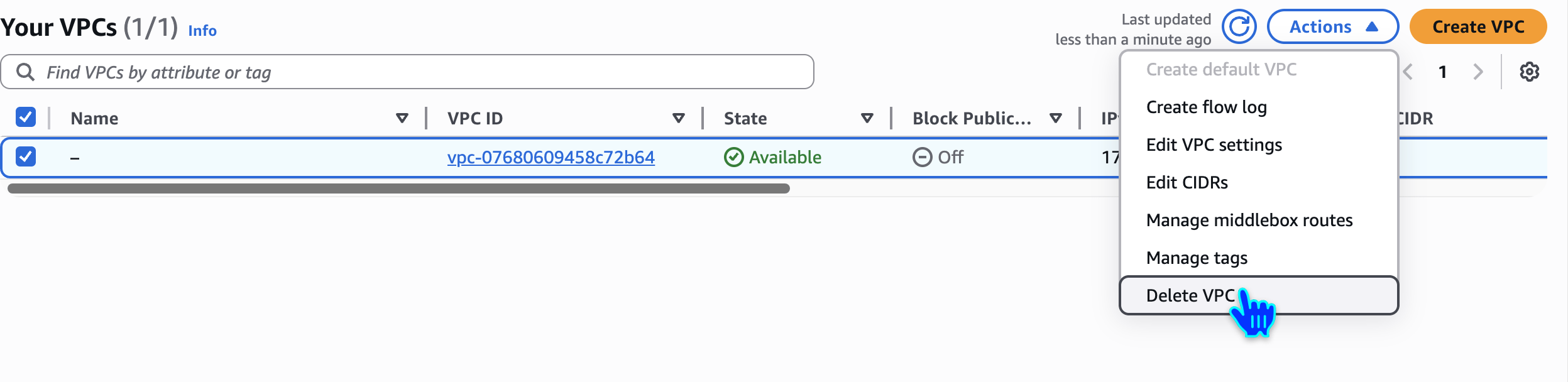
Optional - Delete VPC
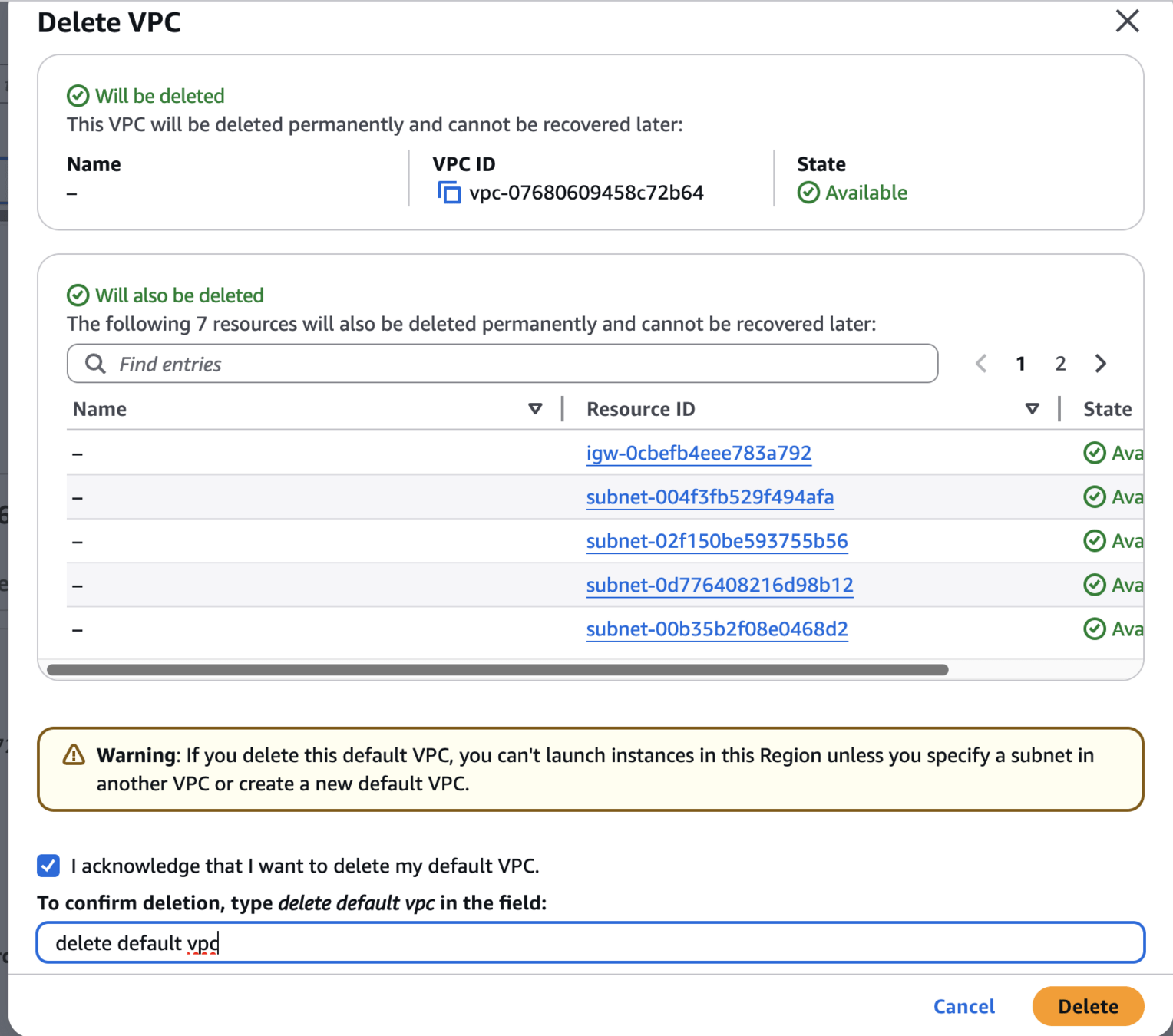
delete default vpc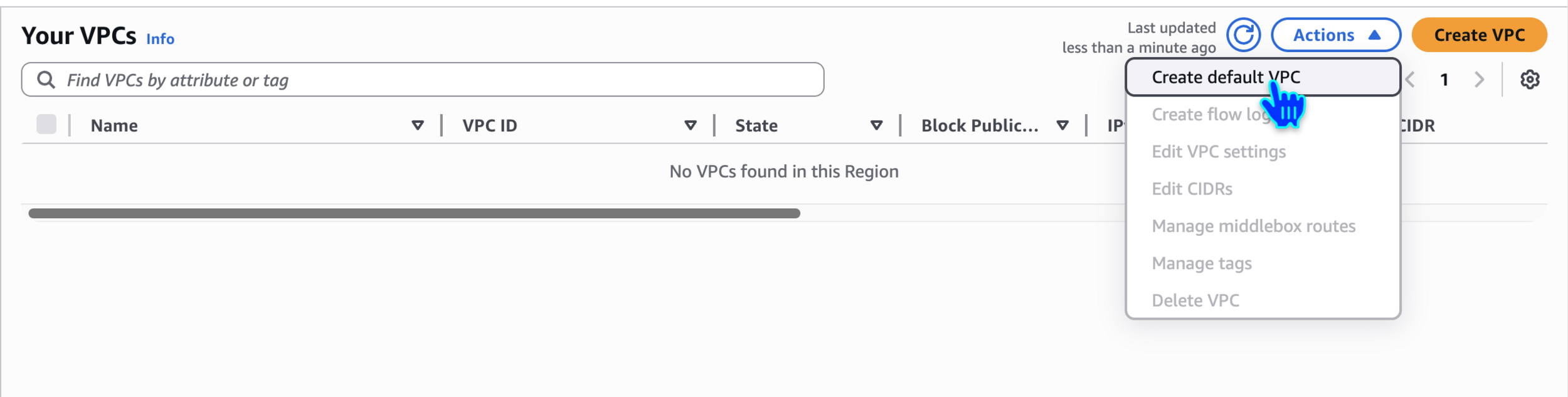
Create default VPC
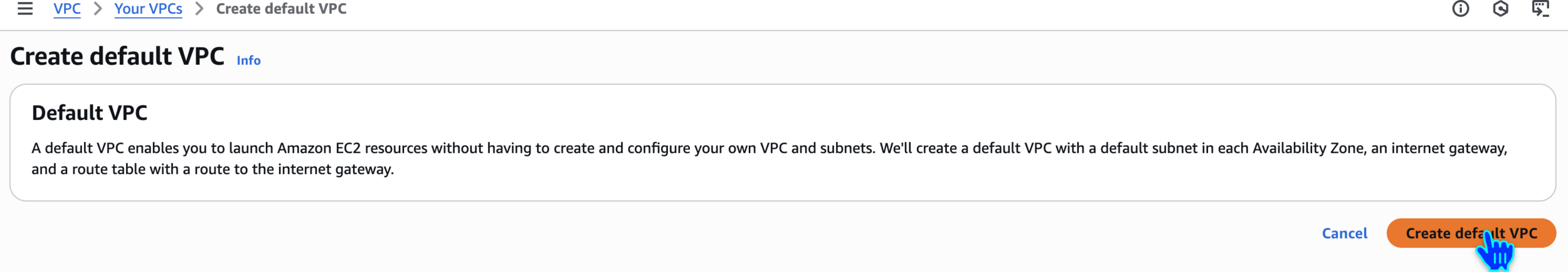
Create default VPC
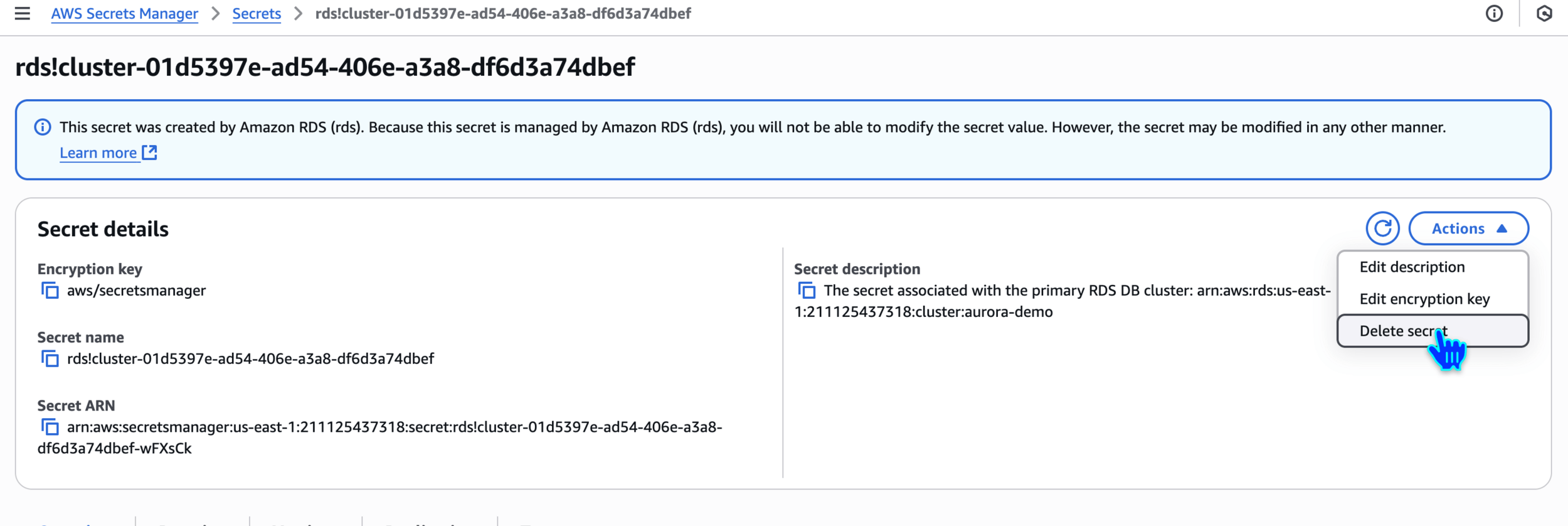
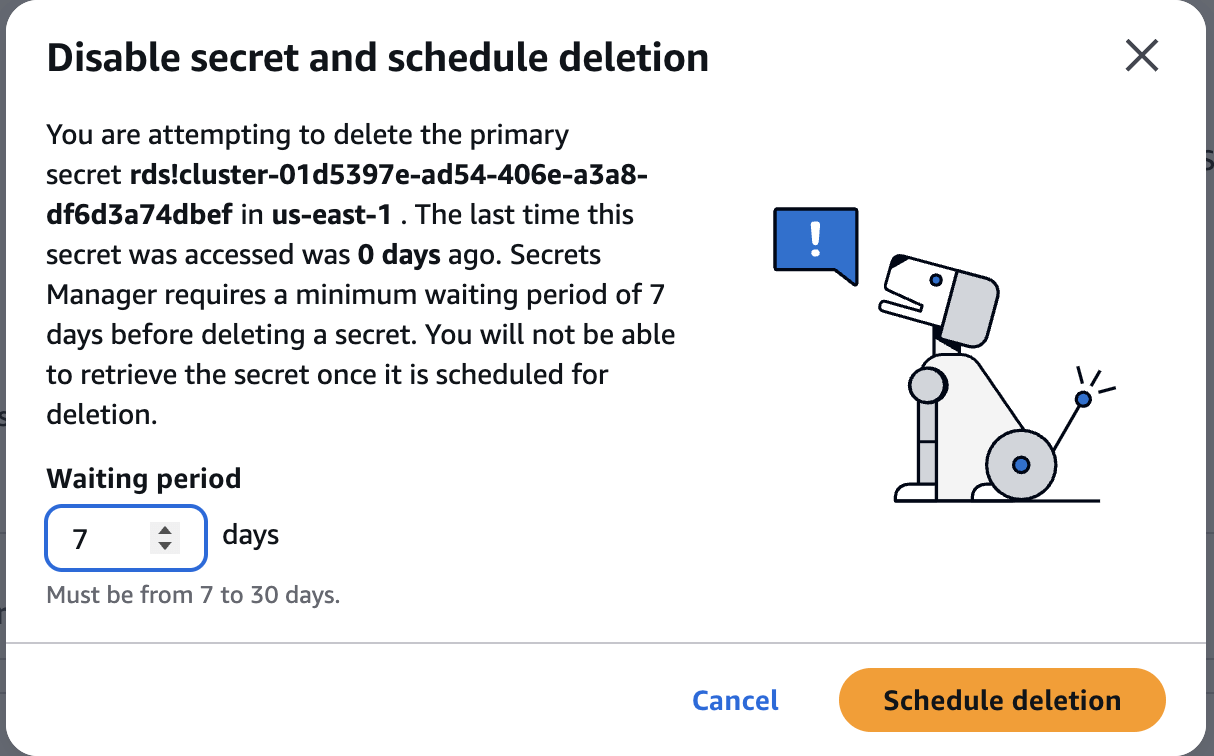
Delete Secret
🙏
Thanks
for
Watching
Amazon Elasticache - Hands-On Demo
By Deepak Dubey
Amazon Elasticache - Hands-On Demo
Amazon Elasticache - Hands-On Demo
- 127



